【AZ-900】What is Azure Role-Based Access Control (RBAC)? Understand how to manage permissions

Hi, I’m Makoto, a freelance engineer.
In this article, I’ll explain Role-Based Access Control (RBAC).
It’s an important mechanism for granting appropriate permissions to users managed by Microsoft Entra ID. Please read to the end.
If you’re not familiar with it, I suggest you read this article first!

Now, let’s get started!
What is Role-Based Access Control (RBAC)?
Role-based access control is a mechanism for managing access permissions to Azure resources. It’s commonly abbreviated as RBAC.
Simply registering a user in the Microsoft Entra ID doesn’t allow them to create, modify, or delete resources such as virtual machines. Access permissions are granted through the RBAC mechanism.
While the term RBAC may sound complex, the concept is similar to managing file permissions in Windows or Linux.
Let’s take a look at a simple example.
The following screenshot shows the Subscription > Resource Groups > Resources hierarchy in an Explorer view. Think of files as resources.
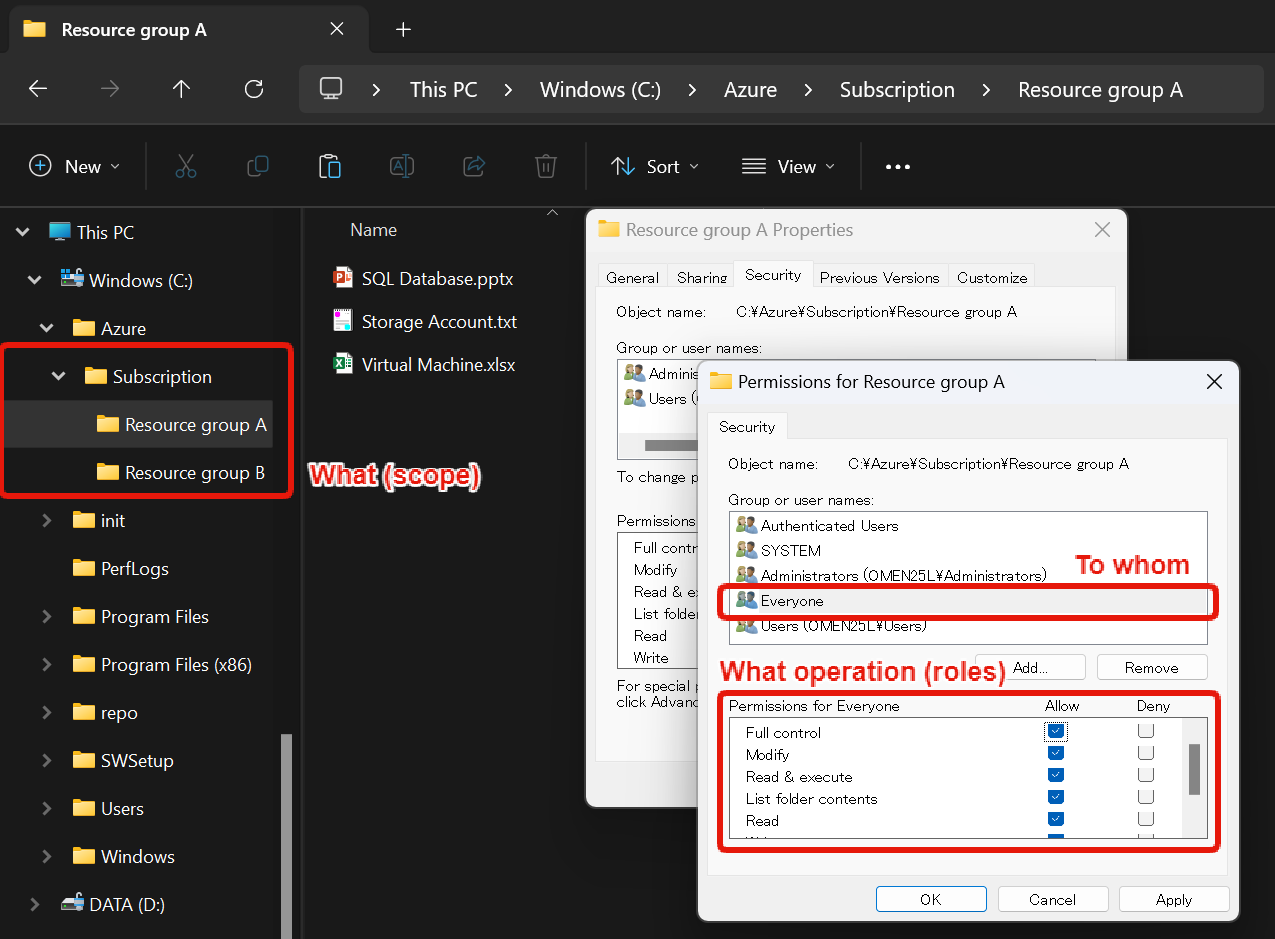

In this example, we’re trying to set full control for Everyone in the “Resource Group A” folder through its properties.
While this is a bit of an extreme example, when you assign access permissions to Azure resources using RBAC, you determine what scope, to whom, and what permissions (roles) to assign.
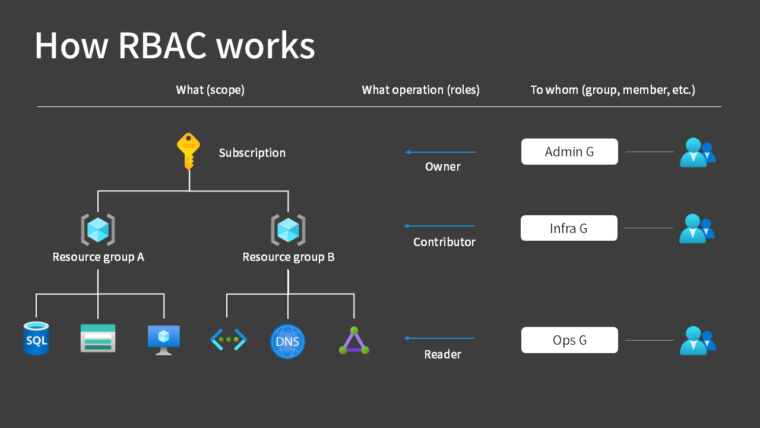

First, select the scope.
The permissions granted to a parent scope are inherited by child scopes.
To learn more about the hierarchy of Azure resources, read this article.



For “to whom”, you can select individual users, but it’s generally better to organize users into groups first, and then grant permissions to the groups.
Then you grant privileges that determine what operations are allowed. In Azure, these permissions are called “roles“.
Azure provides “built-in roles” with general access rules predefined, but users can also create their own roles (custom roles).
Examples of built-in roles include:
- Owner: Allows almost any operation
- Contributor: Allow operations other than grant management
- User Access Administrator: Allow operations that manage user access to Azure resources
- Reader: Read-only
How to Set Up RBAC
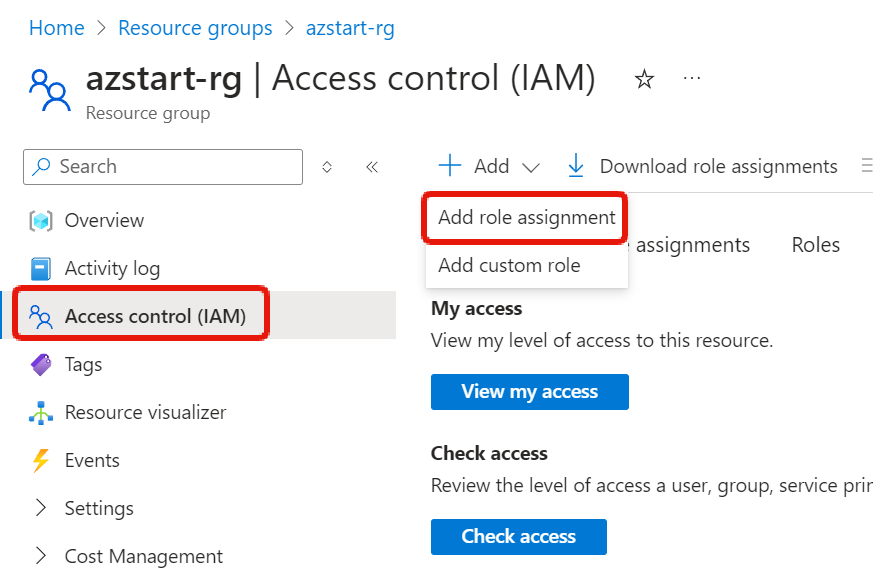
When assigning roles, first open “Access control (IAM)” from the subscription, resource group, or resource screen.
Reference:
IAM stands for “Identity and Access Management,” a common term also used in AWS and GCP.
I’ll write it again, as it may be a little difficult to understand. First, you are taken to the scope resources (all scopes have a common access control menu)
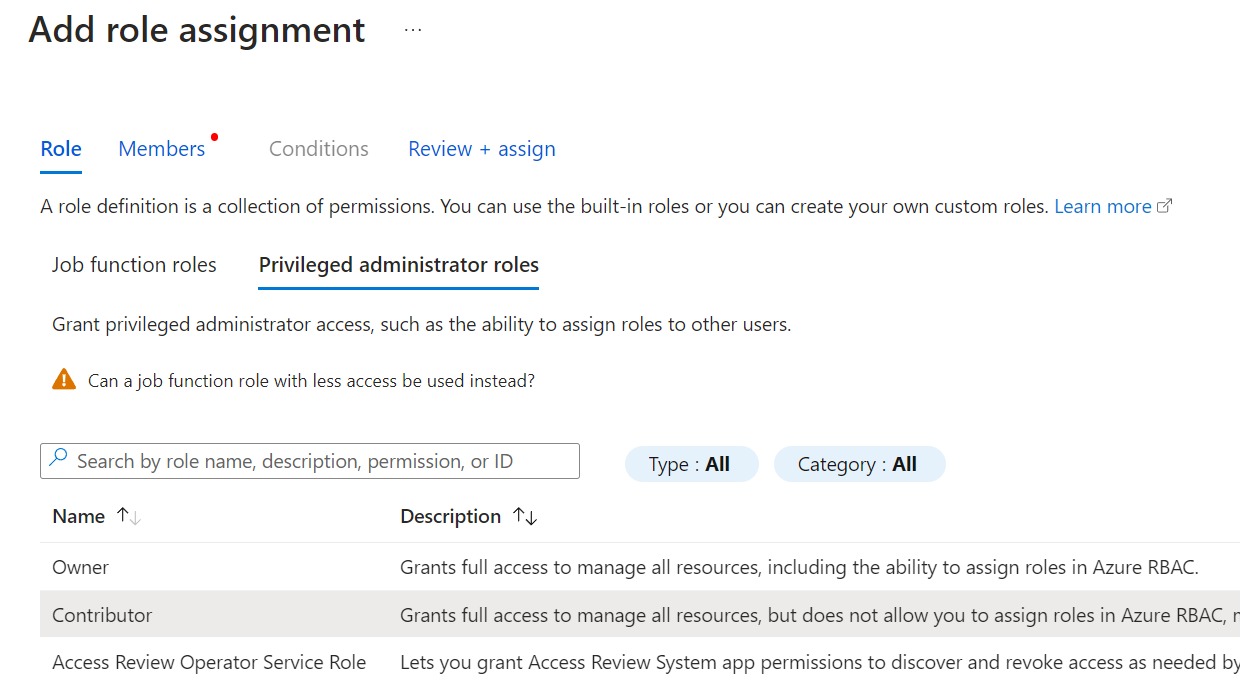
You can start the operation from the Add button → Add role assignment. Here, we’ll set it for a resource group.

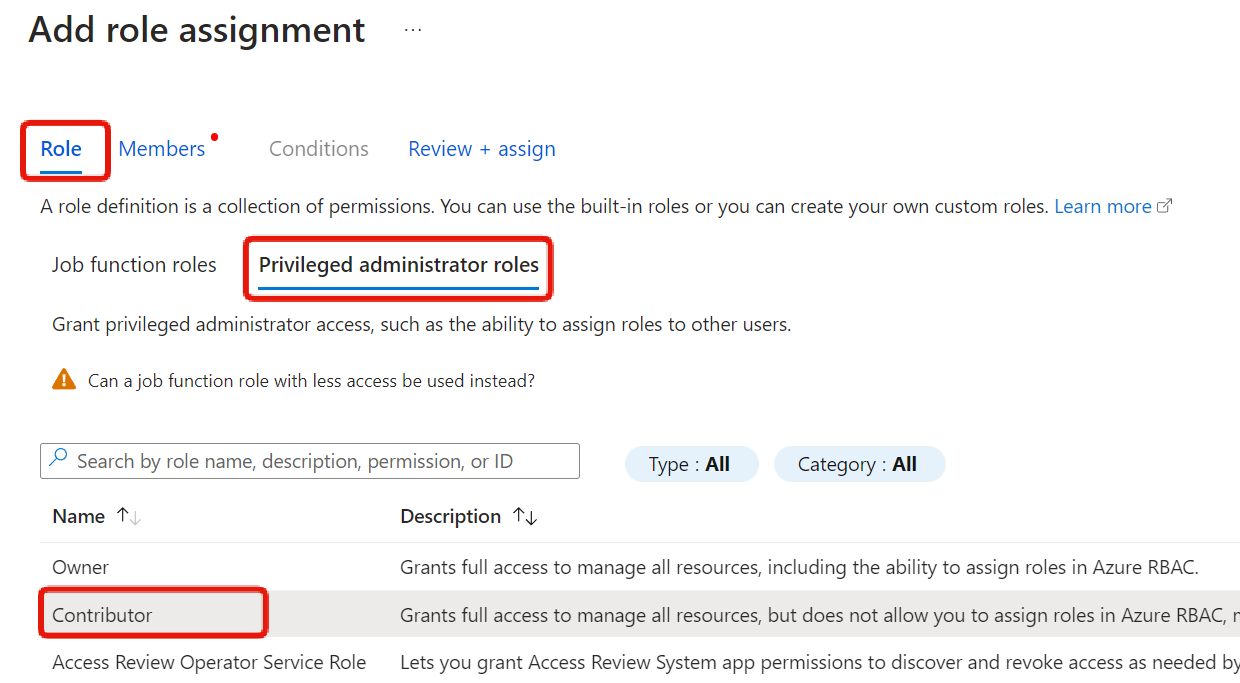
First, select a role. A list of built-in roles will appear. We’ll select Contributor from this list (it’s on the Privileged administrator roles tab).

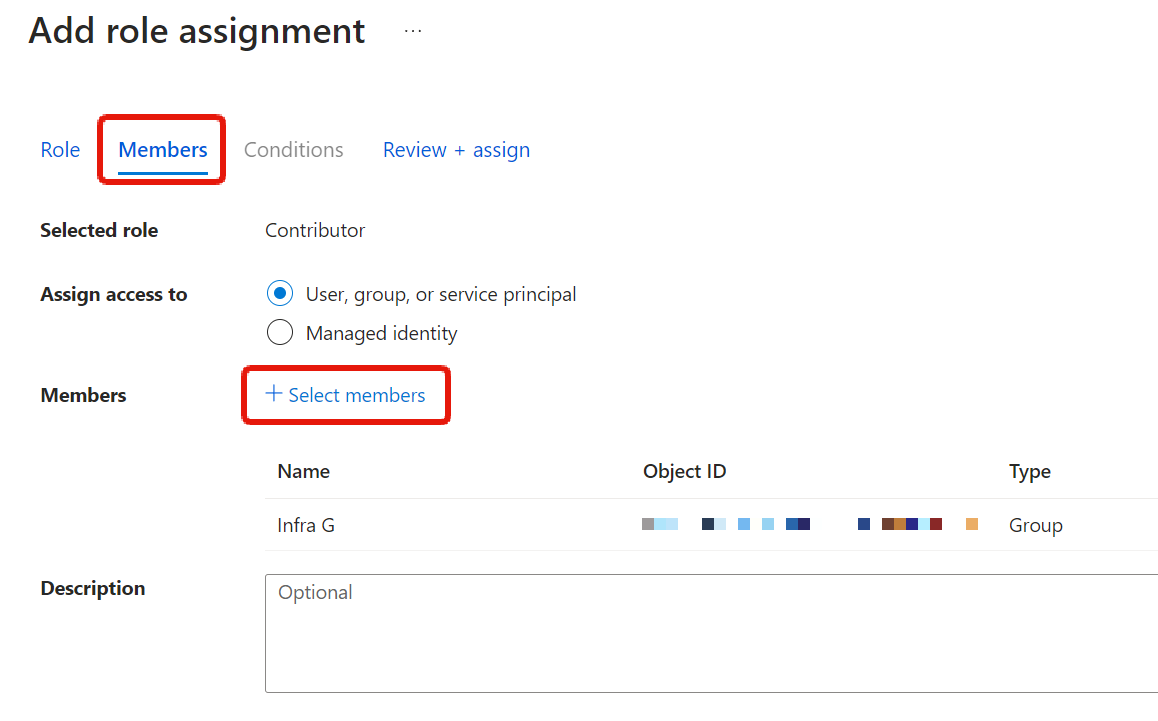
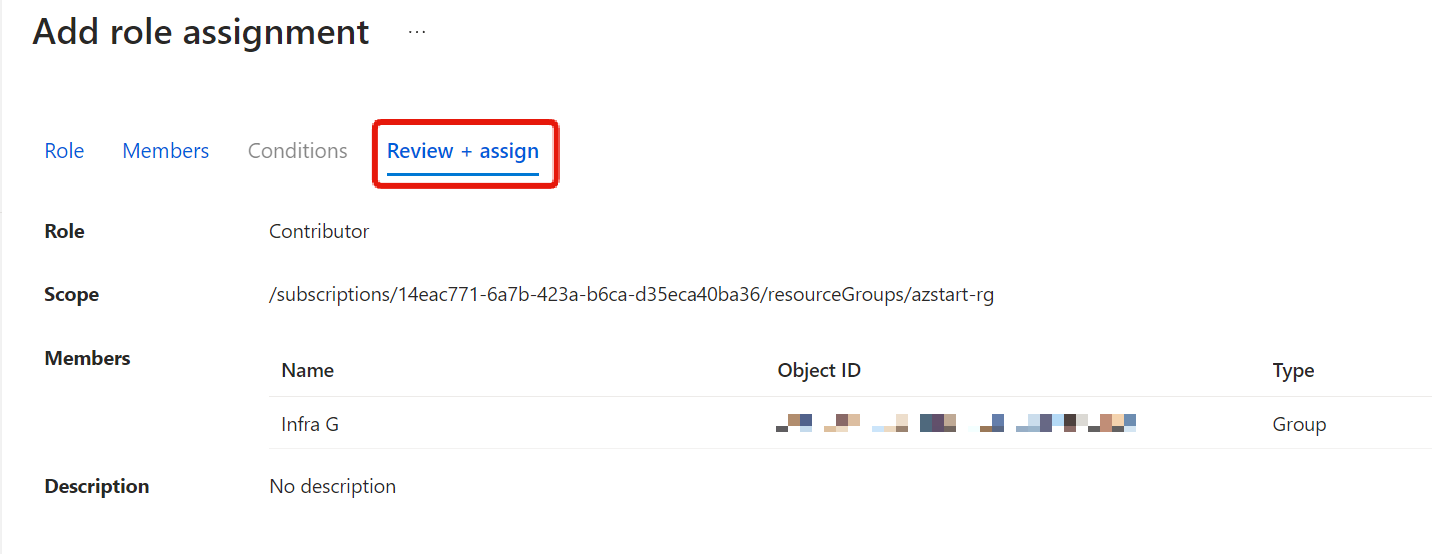
In the next Members tab, select to whom. Here we’ve selected Infra G. We’ll talk about managed identities later.


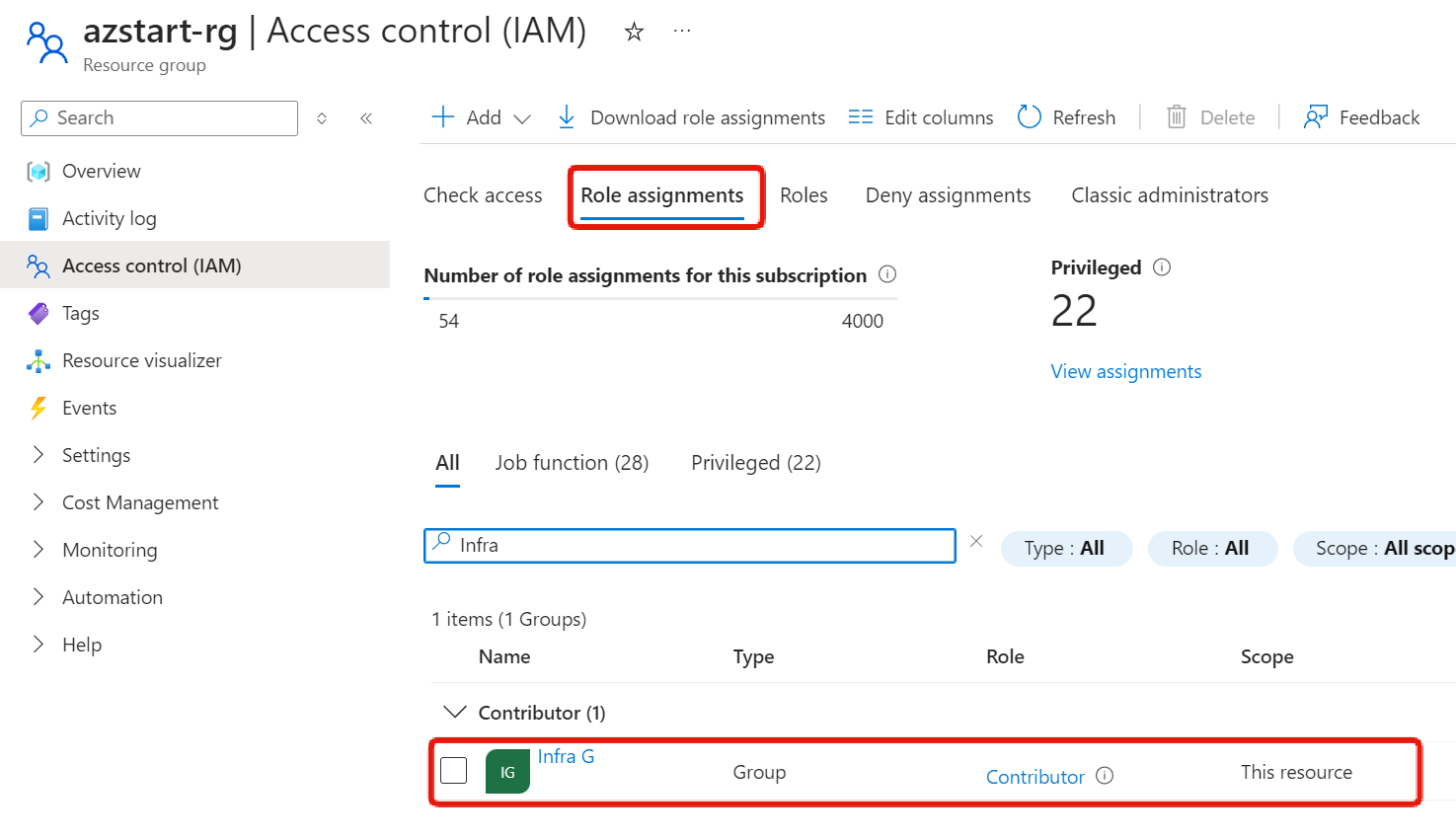

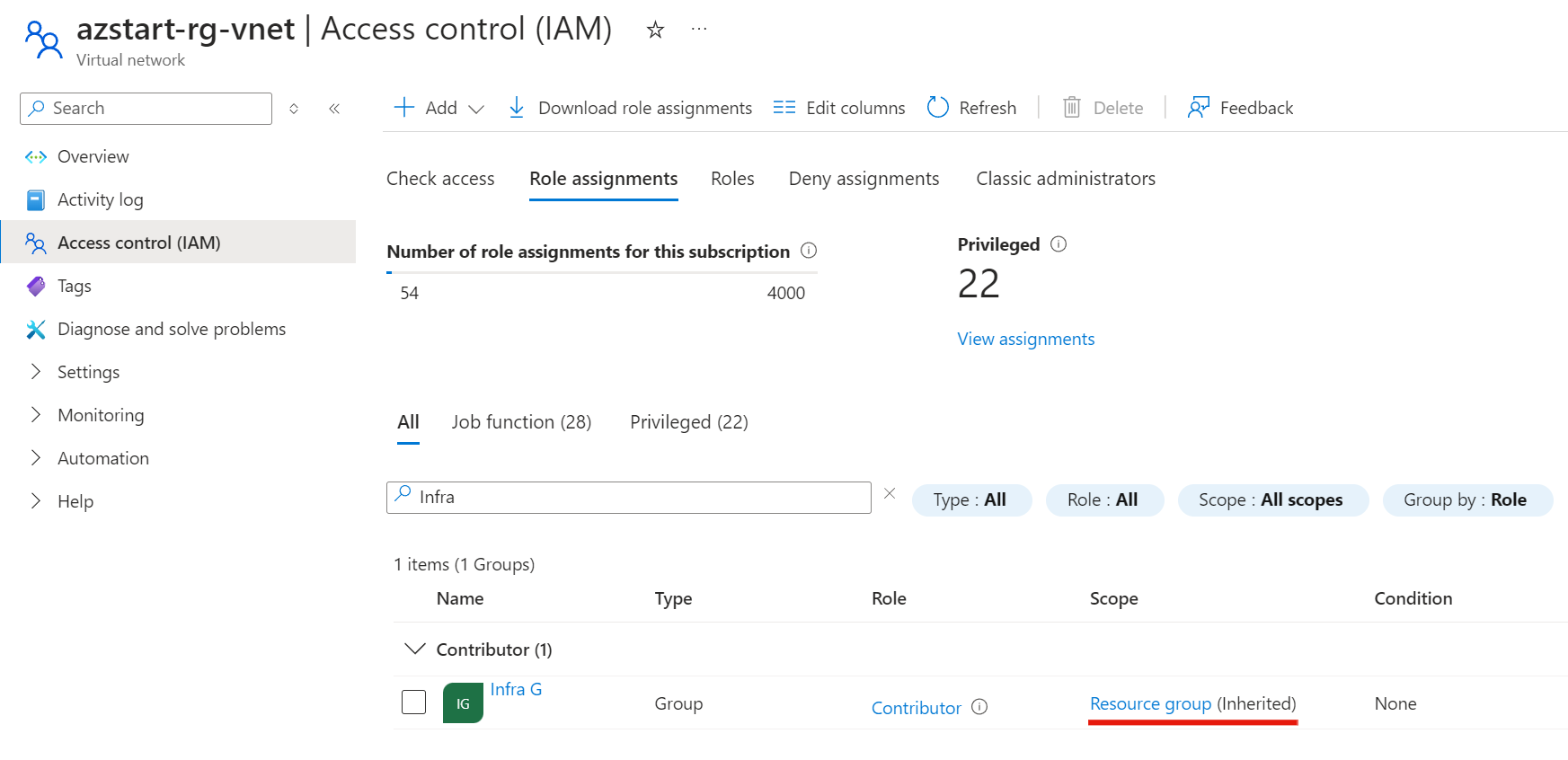
Checking the access control (IAM) of a resource within the resource group (in this case, a virtual network), we can see that the “Contributor” role has been inherited.

What are Managed Identities?
So far we have explained the “to whom” part assuming it is a user, but there are other types of identity IDs in Microsoft Entra ID besides users, such as the following.
| Identity Type | Description |
|---|---|
| User | Organization employees or invited guests accessing from the Azure portal, etc. |
| Service Principal | Identity assigned to applications |
| Managed Identity | Identity assigned to Azure resources such as virtual machines |
| Device | Hardware such as mobile devices or laptops |
For example, if an application running in a virtual machine needs to output logs to blob storage, the virtual machine needs permissions to access the storage.
Let’s discuss managed identities, which are used in such cases.
In this scenario, enabling managed identity for the virtual machine registers an identity for the VM in Microsoft Entra ID so that roles can be assigned to it. (This is similar to the IAM role functionality in AWS)
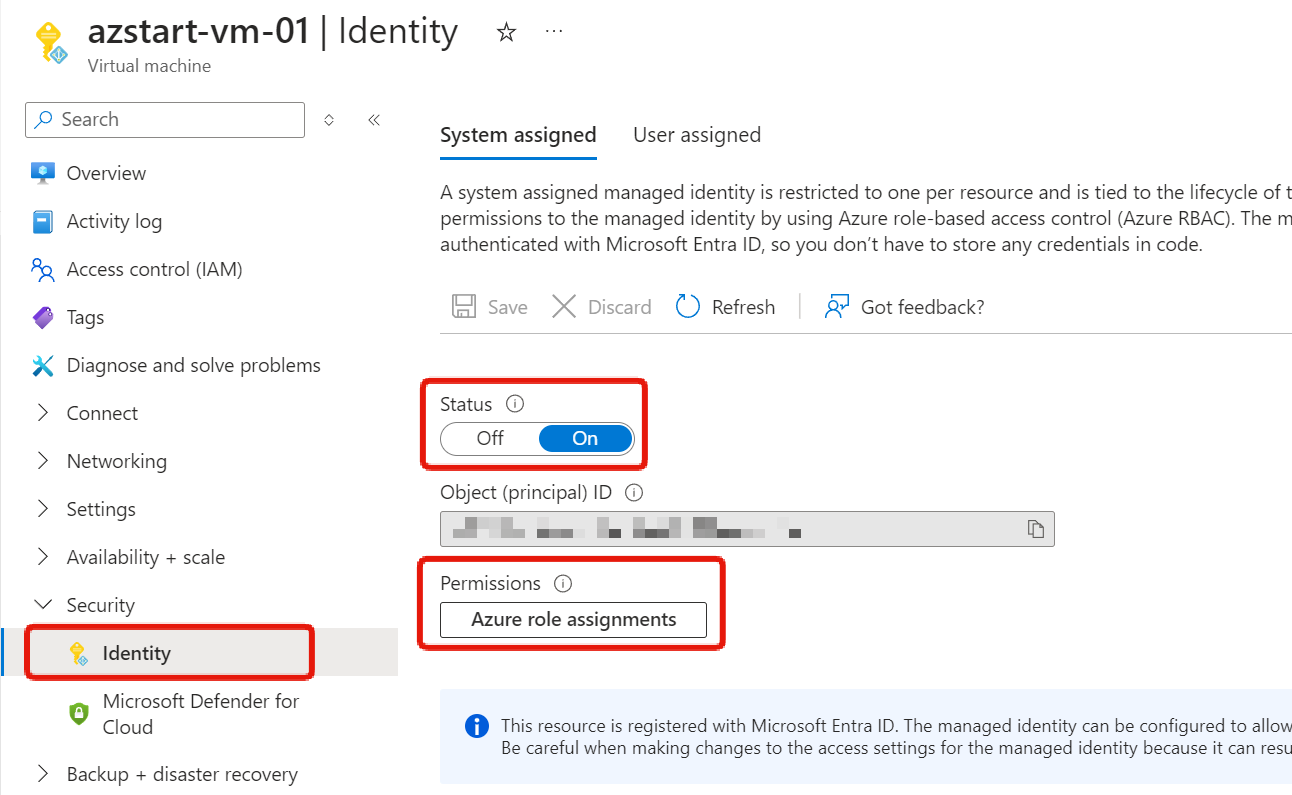

Azure Has Two Types of Roles
This content may not be necessary for the AZ-900 exam, but I’ll add a brief explanation to avoid future confusion.
What’s confusing is that there are actually two types of role = RBAC mechanisms: Azure RBAC and Microsoft Entra RBAC.
As explained in this article, because subscriptions and Microsoft Entra IDs are independent, the operations that can be performed on each are different.
First, as mentioned above, Azure RBAC allows you to assign roles to scopes for creating, reading, modifying, and deleting Azure resources.

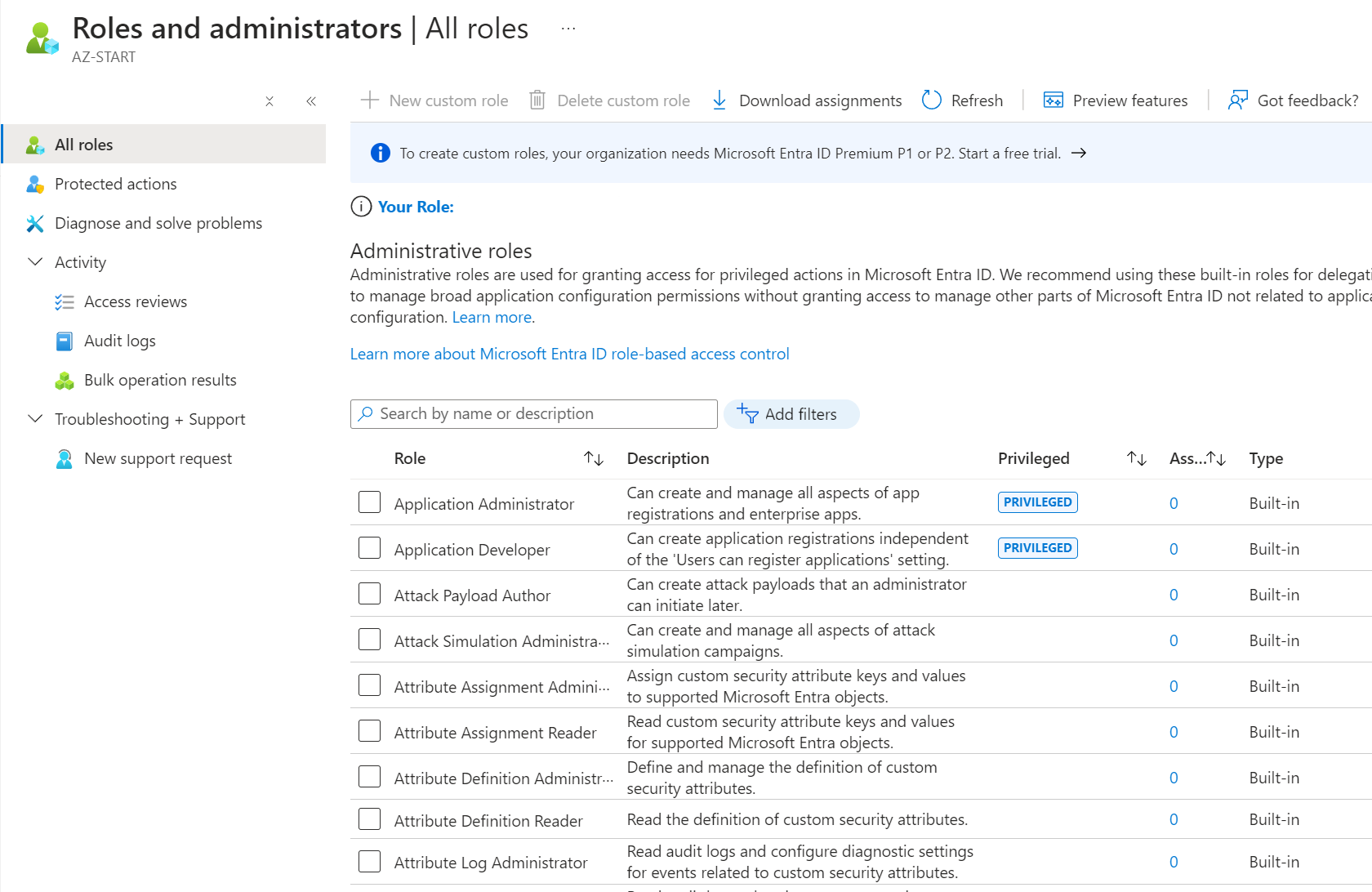
The next screen is the Microsoft Entra RBAC Roles list screen.
You can set roles for ID-related operations such as creating users and groups, resetting passwords, and several built-in roles are also provided here. There’s no hierarchical structure for the assignment target scope. These are Microsoft Entra ID roles.

Administrator accounts have the following privileges. These are the most powerful privileges, allowing everything:
- Subscription: Owner
- Microsoft Entra ID: Global Administrator
Note that roles can be assigned to both subscriptions and Microsoft Entra IDs (permissions are separate).
Key Points:
- Subscription roles are permissions for operating Azure resources
- Microsoft Entra ID roles are permissions related to user management
Summary
In this article, we explained Role-Based Access Control (RBAC). Summarize the key points of RBAC for AZ-900 exam preparation:
- Determine what operations (roles) are allowed, to whom, on what (scope)
- Roles in parent scopes are inherited by child scopes
- There are “built-in roles” that are provided by default and “custom roles” that you can create yourself
- Managed identities are available to assign roles to Azure resources
Identities managed by Microsoft Entra ID and the role mechanism (RBAC) for assigning permissions to those identities are closely related.
It’s considered best practices to organize users into groups and assign the minimum necessary roles to those groups.
When thinking about privilege management, always think of Microsoft Entra ID and RBAC as a set.
That’s all for now. See you next time.












