【AZ-900】What is Network Security Group (NSG)? Explanation of mechanism and precautions!

Hi, I’m Makoto, a freelance engineer.
In this article, I’ll explain the Network Security Group. As the name suggests, it is an important service that forms the basis for strengthening network security. Please read on to the end.
Let’s get started!
Memo:
The Network Security Group is not listed in the exam scope as of the May 2022 revision, but it may be included as part of a virtual machine configuration or as a related topic. Even if it is not included, it is a very important service, so we recommend that you study it together.
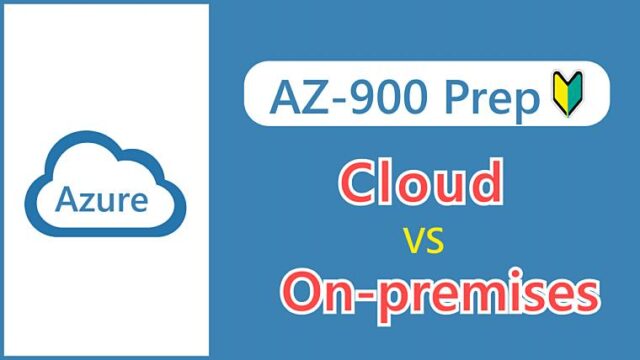
What is Network Security Group (NSG)?
Network Security Groups is a service that allows you to allow or deny traffic sent and received by Azure resources (such as virtual machines) in a virtual network. It is often referred to by the abbreviation NSG.
The ability to allow or deny traffic based on predetermined rules is sometimes referred to as packet filtering or firewall.
NSG is a set of rules for controlling traffic, and rules are defined for both inbound and outbound traffic.
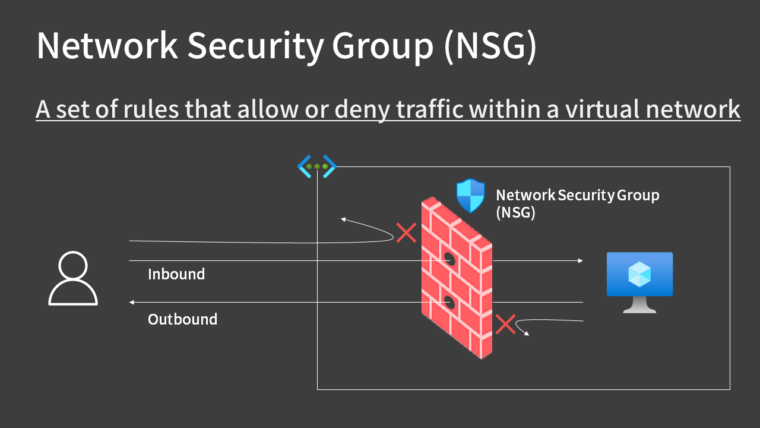
The five-tuple of information used in NSG
NSG uses the following five pieces of information to allow or deny traffic. This combination of five pieces of information is called a “five-tuple“.
- Source IP addresses
- Destination IP addresses
- Source port ranges
- Destination port ranges
- Protocol
Security Rules
A collection of rules is called “Security Rules”, and you can set rules for each inbound and outbound traffic.
- Inbound Security Rules
- Outbound Security Rules
The items that can be entered on each security rule screen are as follows.
| 入力項目 | 説明 |
|---|---|
| Source | Source IP addresses/CIDR ranges |
| Source port ranges | Source port ranges |
| Destination | Destination IP addresses/CIDR ranges |
| Destination port ranges | Destination port ranges |
| Protocol | TCP / UDP / ICMP or Any |
| Action | Allow / Deny |
| Priority | A number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. |
| Name | Rule name (unique within NSG) |
| Description | Description of the rules (optional) |
The following is the screen for adding an inbound security rule. In addition to IP addresses, you can also specify “Augmented security rules” such as service tags for the source and destination (see below).
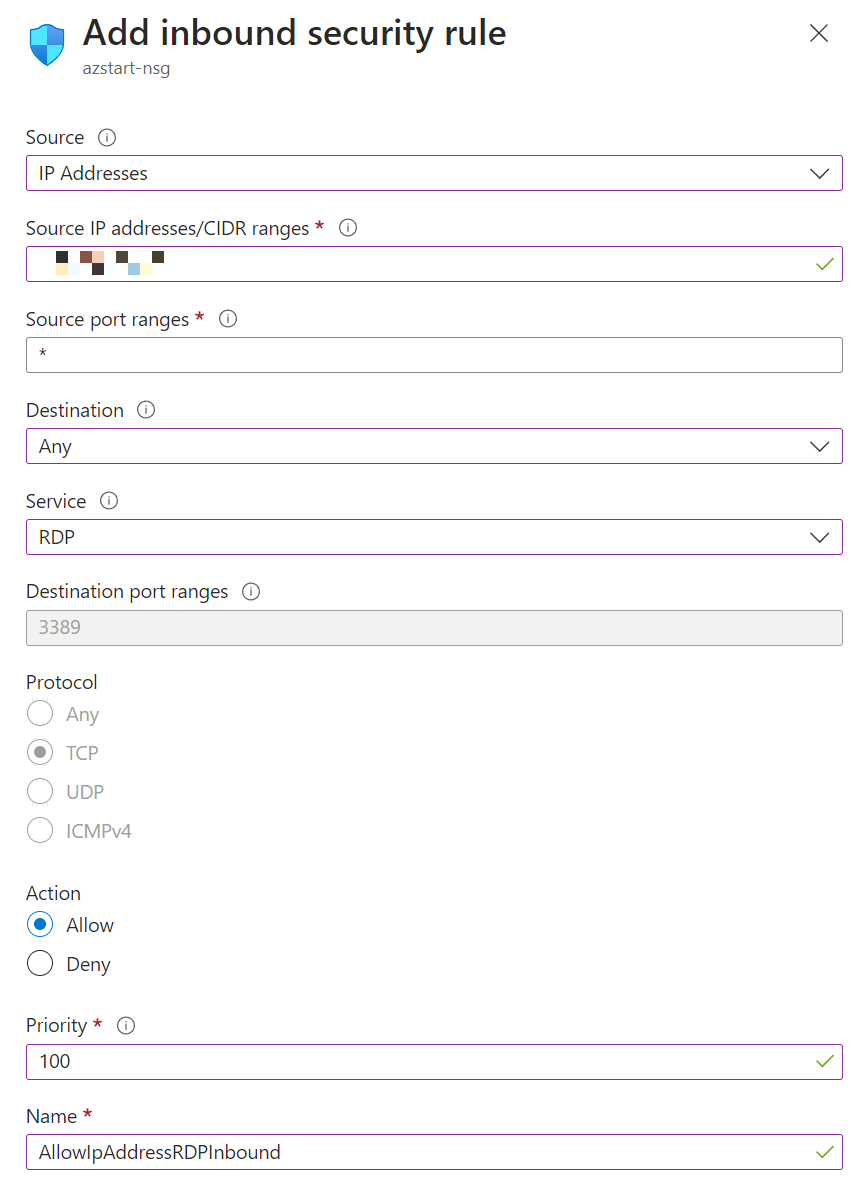
In this example, remote desktop connections are allowed from unique global IP addresses. Even if you don’t remember the port number, you can select the port number and protocol combination by selecting “Service” from the pull-down menu.
Augmented security rules
When there are multiple source and destination IP addresses, it can be cumbersome to specify each one individually or to keep track of them as the IP addresses change.
Augmented security rules make it easy to define multiple IP address ranges, and there are two of them.
- Service Tags
- Application Security Groups
Because IP addresses are grouped from the perspective of services and applications, there is no need to be aware of the IP address values themselves.
Service Tags
Service tag is a group of IP addresses used by Azure services.
For example, if you specify “Storage” as the destination service tag, you can specify the IP address range used by Azure Storage. By the way, if you specify a service tag with a region, you can limit it to the IP addresses of the target region.
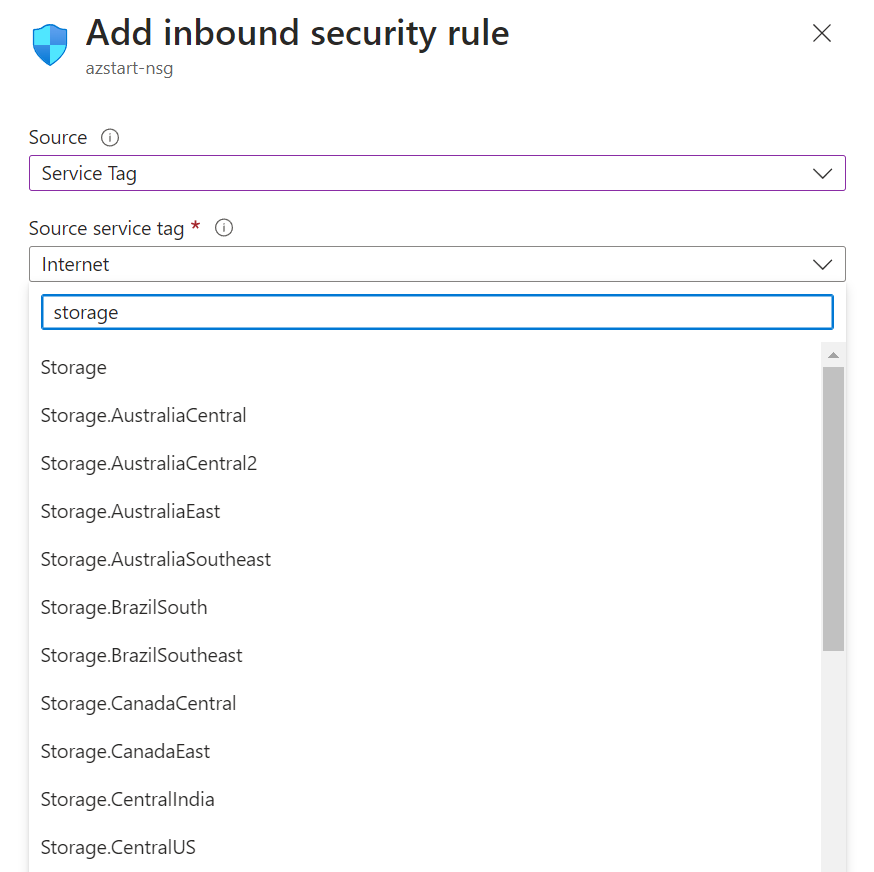
There is also a service tag called “Internet”, which represents the unspecified large number of global IP addresses used on the Internet.
*This includes the global IP addresses used by Azure services.
Application Security Groups (ASG)
Application Security Groups are a feature for grouping virtual machines.
For example, you can create an ASG named “web-sv” to group web servers, and then assign multiple virtual machines to this web-sv so that you can specify them all together in the Security Rules screen.
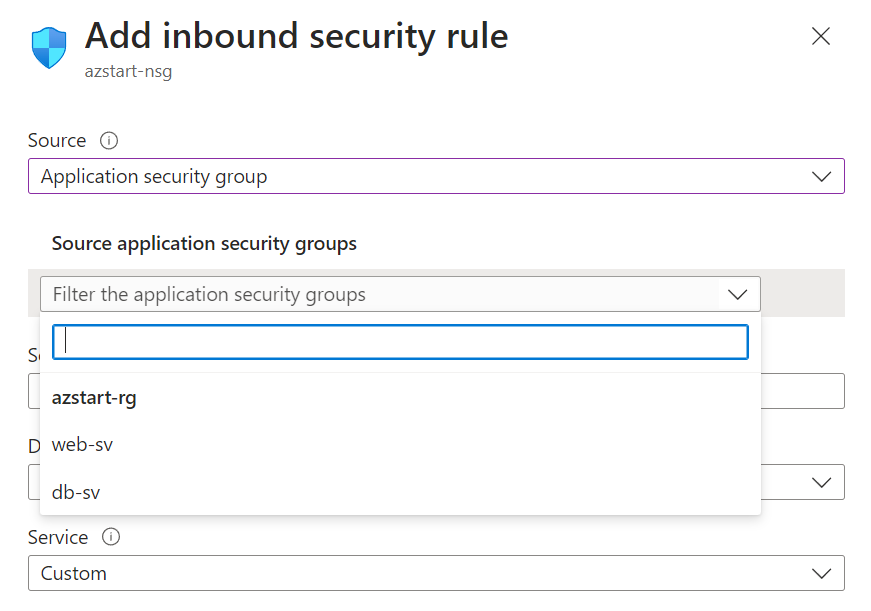
Although the name is similar to NSG, it is simply a way to group virtual machines. Also, it is pointless to just create an ASG, so you must be careful not to forget to assign virtual machines.
NSG Association Patterns
NSG can be associated with a subnet, a network interface, or both. You can also select None, but this is not recommended because all traffic is allowed.
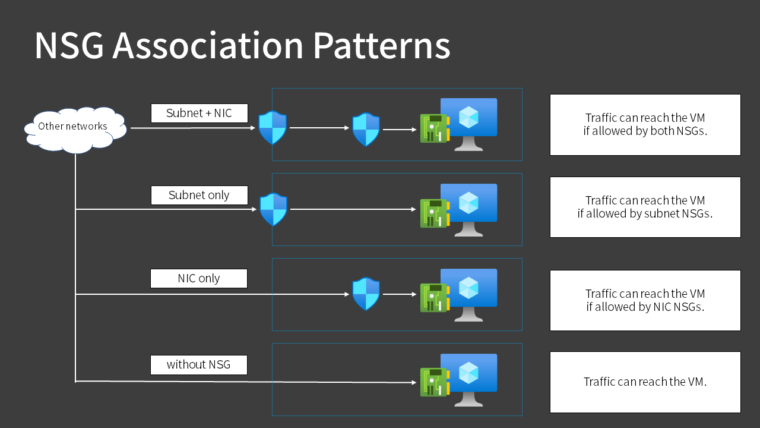
When you assign it to a subnet, it applies to all Azure resources (such as virtual machines) that belong to that subnet.
Key Points:
Associated with network interface
Applies only to a single virtual machine
Associated with subnet
Applies to all virtual machines on the subnet
As stated in the official documentation, associating NSG with both is not recommended because it complicates management. I think it is easier to understand if you separate subnets by usage and basically assign them to subnets.
Unless you have a specific reason to, we recommend that you associate a network security group to a subnet, or a network interface, but not both. Since rules in a network security group associated to a subnet can conflict with rules in a network security group associated to a network interface, you can have unexpected communication problems that require troubleshooting.
Source:Intra-Subnet traffic
Note that you cannot associate an NSG with the entire virtual network. The association target is either a subnet or a network interface.
Also, NSG is only for traffic control and does not have the ability to encrypt data sent and received. Encryption is a different matter, although it is the same security.
Encryption is implemented using operating system or application features such as HTTPS or IPSec. Be careful not to confuse them.
Points to note when associating NSG with a VM
Be careful about the association when creating a VM
Where to associate the NSG is important from a design perspective.
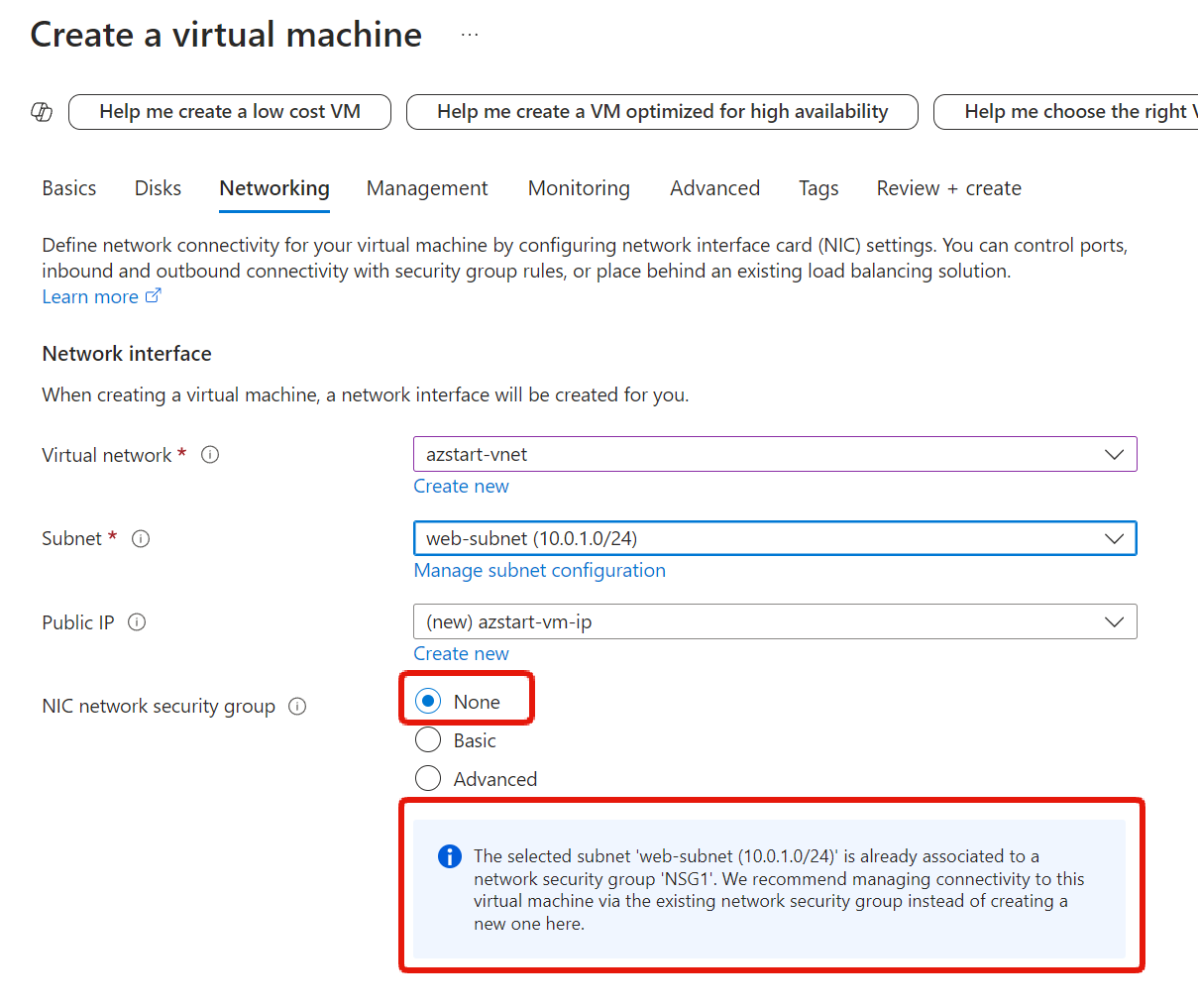
As we saw in the hands-on article about creating a virtual machine and connecting to it via remote desktop, If you create the NSG along with the virtual machine in the virtual machine creation procedure, it will be associated with the network interface.
https://az-start.com/create-windows-vm-hands-on/
To be precise, the NSG specified in the virtual machine creation screen is a setting for associating it with the network interface.
Once you’re more familiar with the process, you can try to create the NSG and security rules first, then associate them with the subnet, and then proceed with “None” on the virtual machine creation screen.
If there is an association with the selected subnet, the wizard will display “The selected subnet is already associated to a network security group” as shown below. If you look closely, you’ll see that the parameter name is “NIC network security group”.
Any permissions should be limited to the test environment
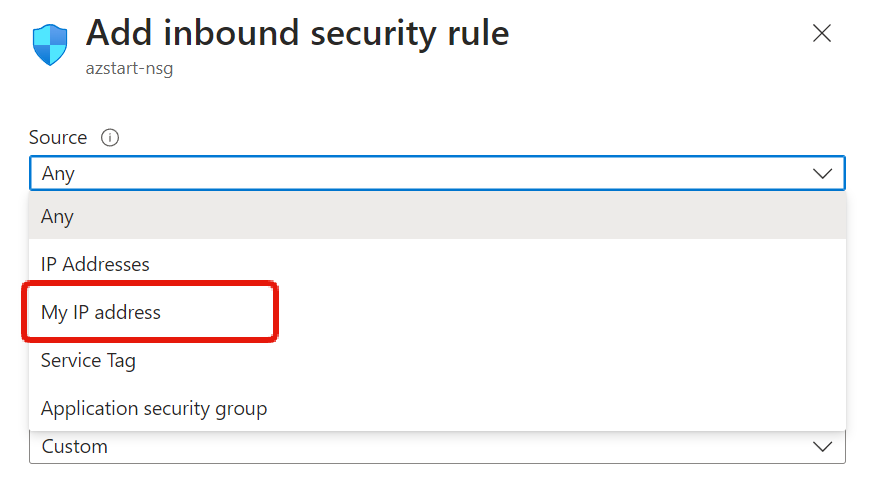
The “Any” setting for source and destination means “all”.
If an administrator connects to Windows via RDP (3389) and to Linux via SSH (22), they will need to allow these connections in NSG, but initially, they will likely create an “Any” setting for the source IP address.
This is fine for temporary environments, but it is not good from a security perspective. Once you get used to it, you should check the global IP address of your home environment using WhatIsMyIP.com or similar, and specify it as the source IP address.
Reference:
Currently, if you specify “My IP address” as the source, you can register the global IP address of the environment you are connecting from.
To begin with, if you use the managed jump box service called Azure Bastion, you won’t even need to open ports, but since that’s outside the scope of AZ-900 exam, we’ll introduce that in a separate article.
Default security rules
There are several “Default security rules” that are registered in the NSG from the beginning. I don’t think they are asked about on the AZ-900 exam, but
I will explain so that this does not happen.
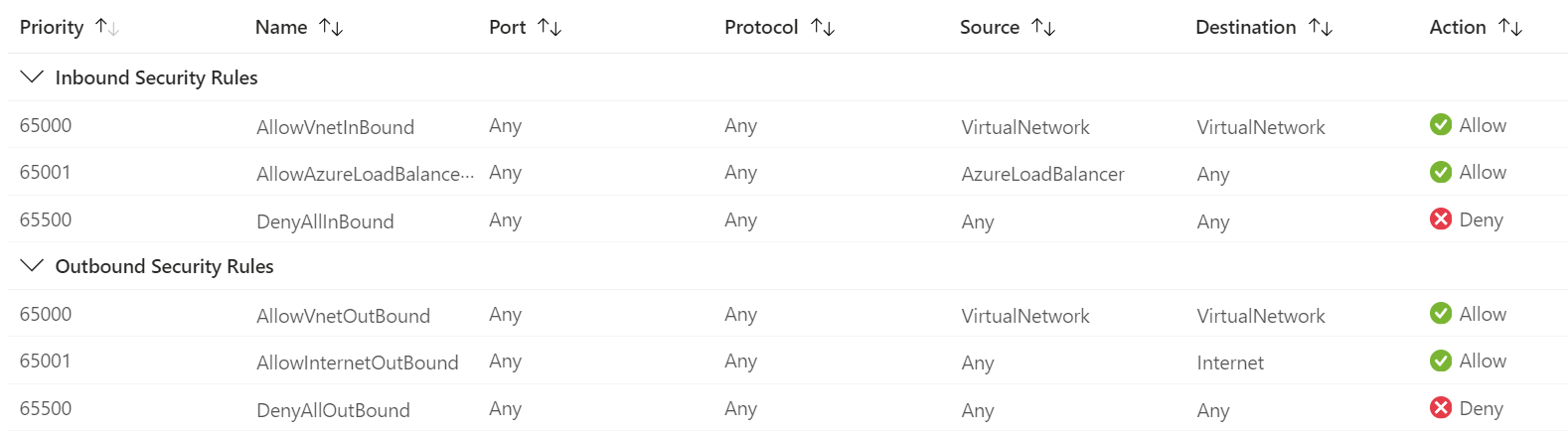
If I were to summarize it now, it would be like this.
- Allows inbound and outbound traffic between resources on the same virtual network. (*)
- Health checks from the load balancer are allowed.
- Traffic to the Internet is allowed.
- Everything else is denied.
*Although communication between virtual networks is allowed, in order to communicate between different virtual networks, it is necessary to connect them using virtual network peering, etc., as explained in this article, so here we have specified “on the same virtual network”.
Inbound Security Rules
- AllowVNetInBound
- Traffic between virtual networks is allowed.
- AllowAzureLoadBalancerInBound
- Traffic is allowed for the load balancer to monitor the health of the target server.
- DenyAllInbound
- All inbound traffic is denied.
Outbound Security Rules
- AllowVnetOutBound
- Traffic between virtual networks is allowed.
- AllowInternetOutBound
- Traffic to the Internet is allowed.
- DenyAllOutBound
- All outbound traffic is denied.
Summary
In this article, we have explained the overview of the Network Security Group (NSG) and the parameters for setting it up.
Network security groups are important for the secure operation of virtual machines. Network Security Groups also appear in other Azure resources that are deployed in virtual networks.
Let’s make sure we understand the basics of Network Security Groups by referring to this article!