【AZ-900】Public vs. Private Endpoints: Understanding PaaS Connection Options
Hi, I’m Makoto, a freelance engineer.
In this article, I’ll explain about endpoints for connecting to Azure PaaS services. Service endpoints may not be part of the scope of the exam, but I’ll explain them as well for convenience.
- Public Endpoint
- Service Endpoint
- Private Endpoint
I’ll explain not only the overview of each endpoint but also the internal mechanisms and configuration steps. Please read to the end.
Let’s get started!
Endpoint Comparison Summary
Let’s start with the bottom line. The three endpoints can be summarized as follows:
| Endpoint | Route |
|---|---|
| Public Endpoint | Connect over the Internet using a public IP address |
| Service Endpoint | Connect over the Azure backbone using a public IP address |
| Private Endpoint | Connect over the Azure backbone using a private IP address |
Both service endpoints and private endpoints are means to connect securely without going through the Internet, with the difference being whether they use public or private IP addresses.
I’ll explain this in more detail later, but for AZ-900 exam preparation, you should first understand the difference between public and private endpoints.
What is a Public Endpoint?
First, let’s understand the meaning of the term “endpoint”.
The term “endpoint” refers to a physical device at the end of a computer network, but in the context of the cloud, it is safe to assume that it refers to the “URL” for connecting services.
Major Azure PaaS services are designed to be accessed over the Internet by default, and when you connect to URLs like *.windows.net, they resolve to public IP addresses.
| Services | Example connection URL |
|---|---|
| Blob Storage | aaa.blob.core.windows.net |
| App Service | bbb.azurewebsites.net |
| SQL Database | ccc.database.windows.net |
Reference:
While disk storage for virtual machines in Azure Storage is classified as IaaS, other data services such as BLOB storage are primarily classified as PaaS.
A public endpoint refers to the URL associated with each service, which can also be described as the public IP address that serves as the connection point. The blue circle in the figure represents the image of a public endpoint.
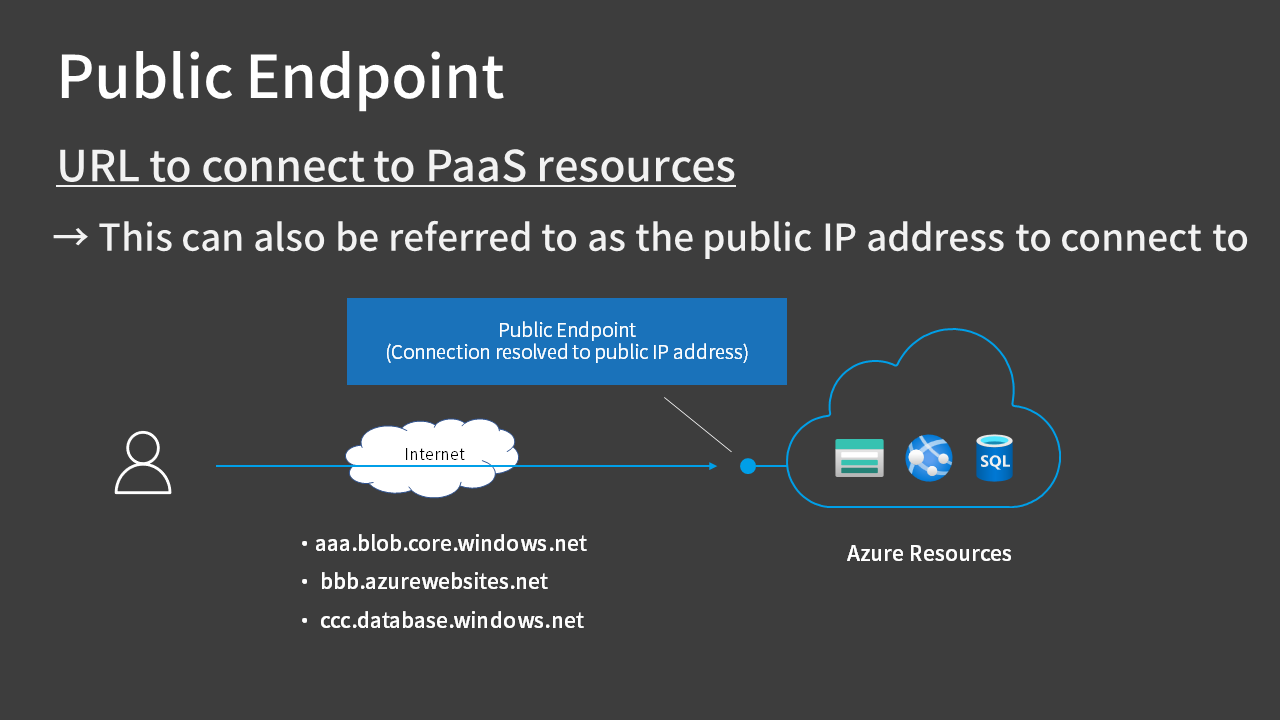
Connecting over the Internet using a public IP address means that if security settings are lax, there’s a risk that anyone can connect.
To increase the overall security level of a system, it is often required that it be able to connect to a closed network without going through the Internet.
With this in mind, the “private endpoint” was introduced.
What is a Service Endpoint?
Before we talk about private endpoints, let’s talk about service endpoints. These are the equivalent of VPC endpoints (gateway type) in AWS.
While it’s not specifically mentioned in the AZ-900 exam scope, I recommend understanding it along with private endpoints as they are often compared, which will be beneficial for your future.
Using a service endpoint allows you to connect to PaaS resources without going through the Internet. Another feature is that it can be used for free.
Here’s an excerpt from the official documentation that explains service endpoints:
Virtual Network (VNet) service endpoint provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network. Endpoints allow you to secure your critical Azure service resources to only your virtual networks.
In essence, it states that two things become possible:
- Traffic is routed through the Azure backbone network.
- Access can be restricted to originate only from specific virtual networks.
Here’s a diagram to illustrate:
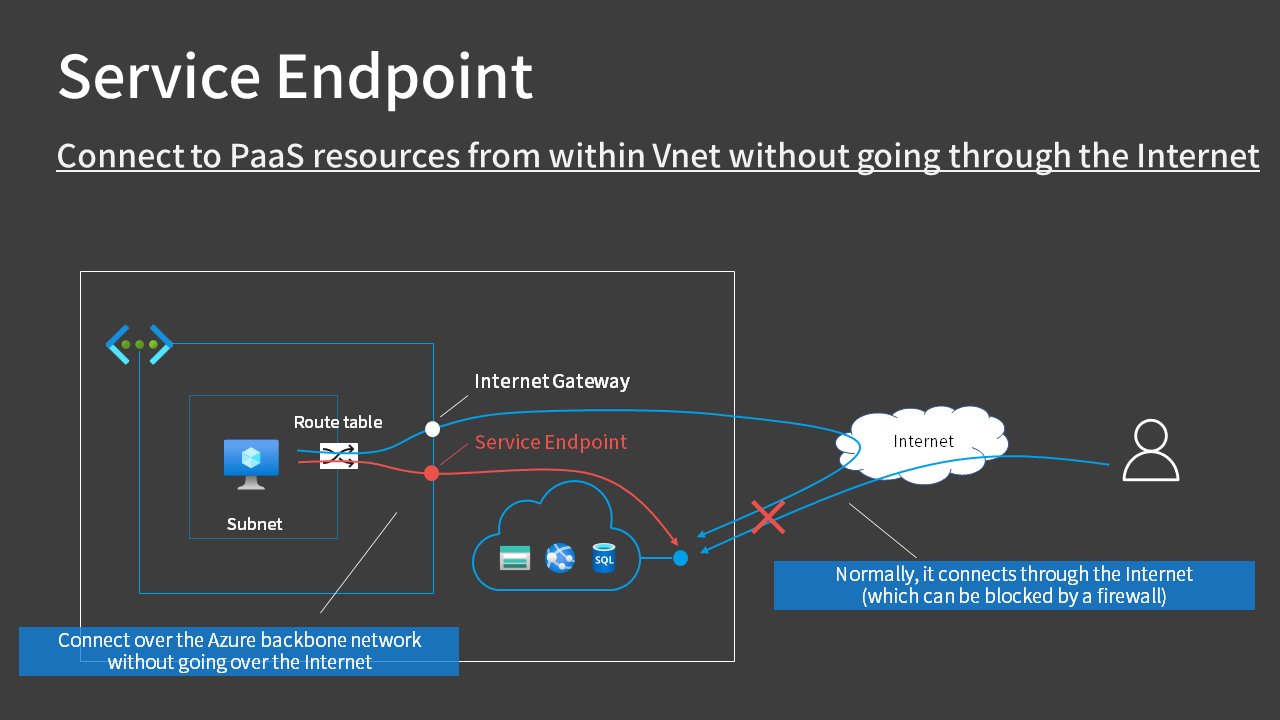
Routing through the Azure backbone applies to connections from the virtual network. In the example in the figure, when a virtual machine tries to connect to a resource, it can connect directly without going through the Internet.
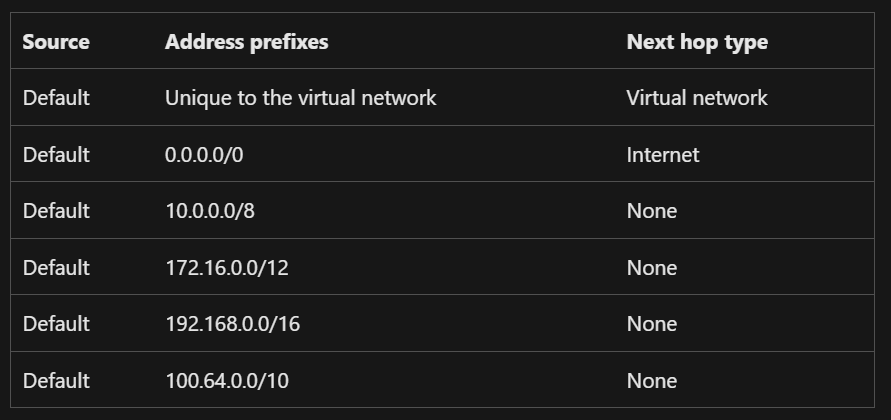
By default, a route table called “system route” is set for each subnet in the virtual network, and the next hop for 0.0.0.0/0, i.e., for public IP addresses, is set to “Internet”. (White circle in the figure)
Source: Virtual network traffic routing
However, when you configure a service endpoint, a connection point through the Azure backbone is created (red circle in the figure) and a route is added where the next hop for connecting to the public IP addresses of the specified service becomes “service endpoint”.
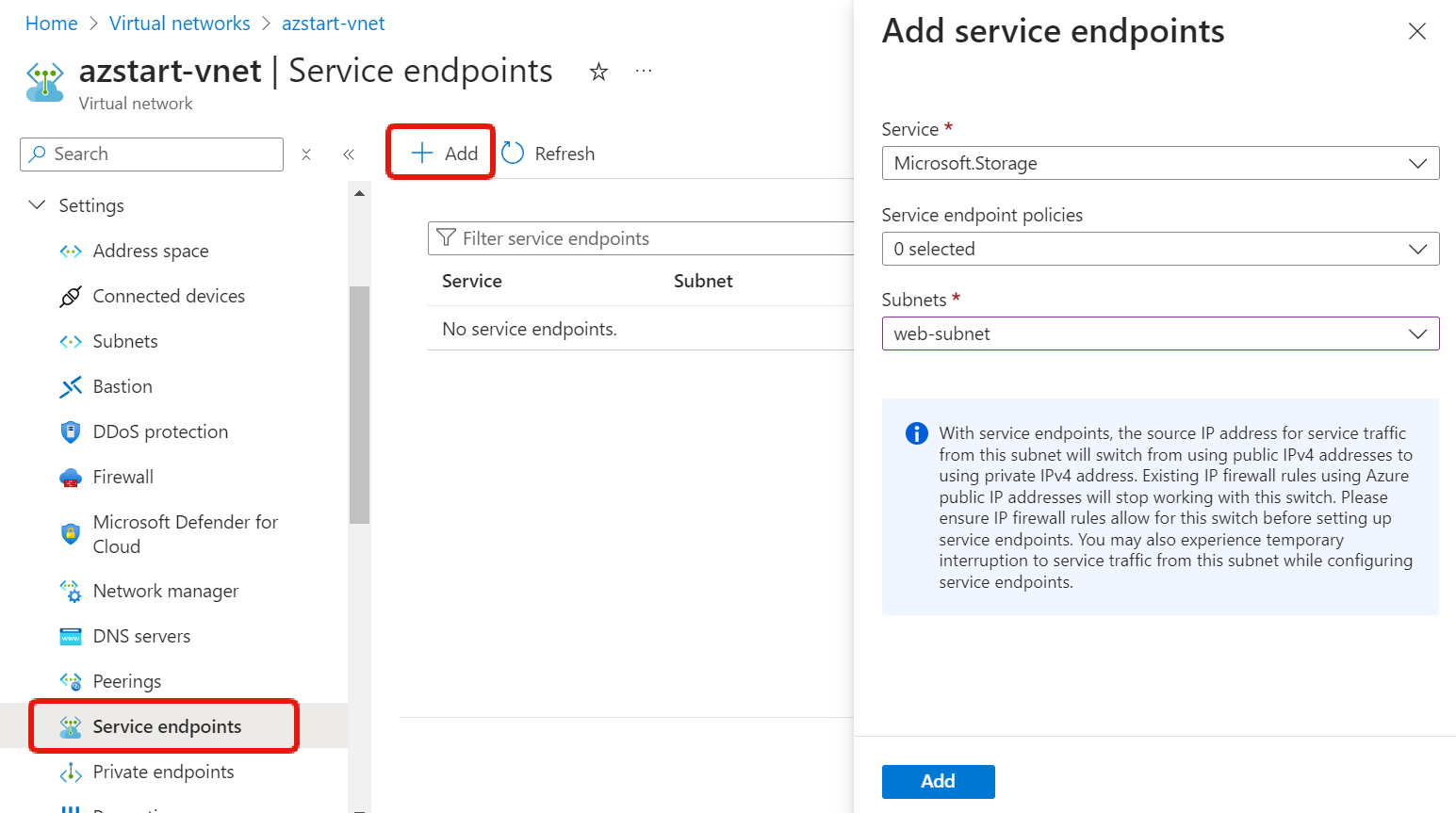
Here’s the service endpoint addition screen in the virtual network menu. In this example, we’ll add Azure Storage (Microsoft.Storage).
 Here’s the effective routes screen in the network interface menu of the virtual machine. A route for connecting to Azure Storage has been added.
Here’s the effective routes screen in the network interface menu of the virtual machine. A route for connecting to Azure Storage has been added.
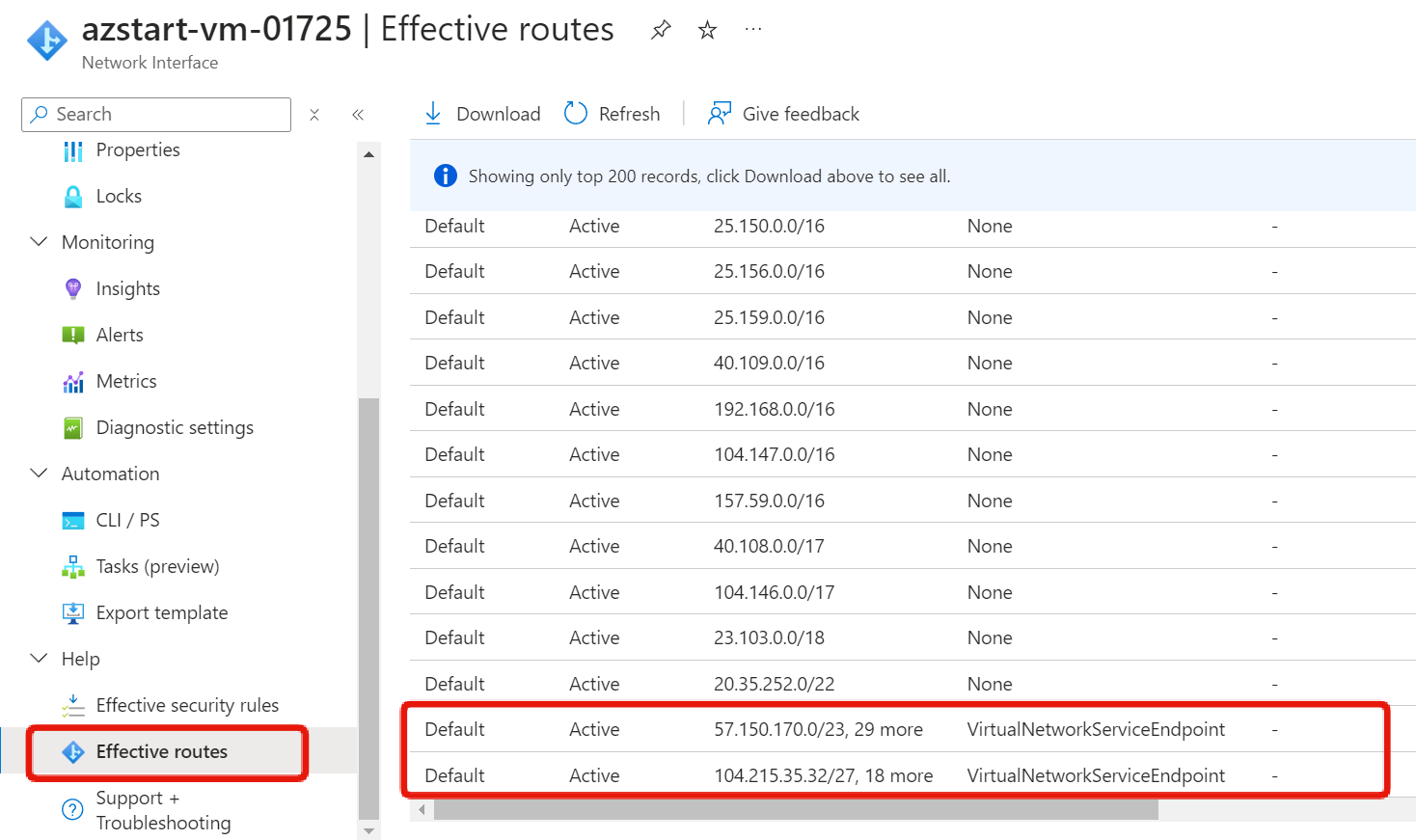
Reference:
When going out to the Internet, the source IP is translated (SNAT) to a public IP address, but when going through a service endpoint, you can connect with a private IP address, so a public IP address is not necessary.
Service endpoints can also be used for access control with firewalls.
When changing the public network access setting to “Enabled from selected virtual networks and IP addresses”, you can limit the source to virtual networks (subnets) that have service endpoints.
The following screen shows adding a subnet from the network menu of a storage account.
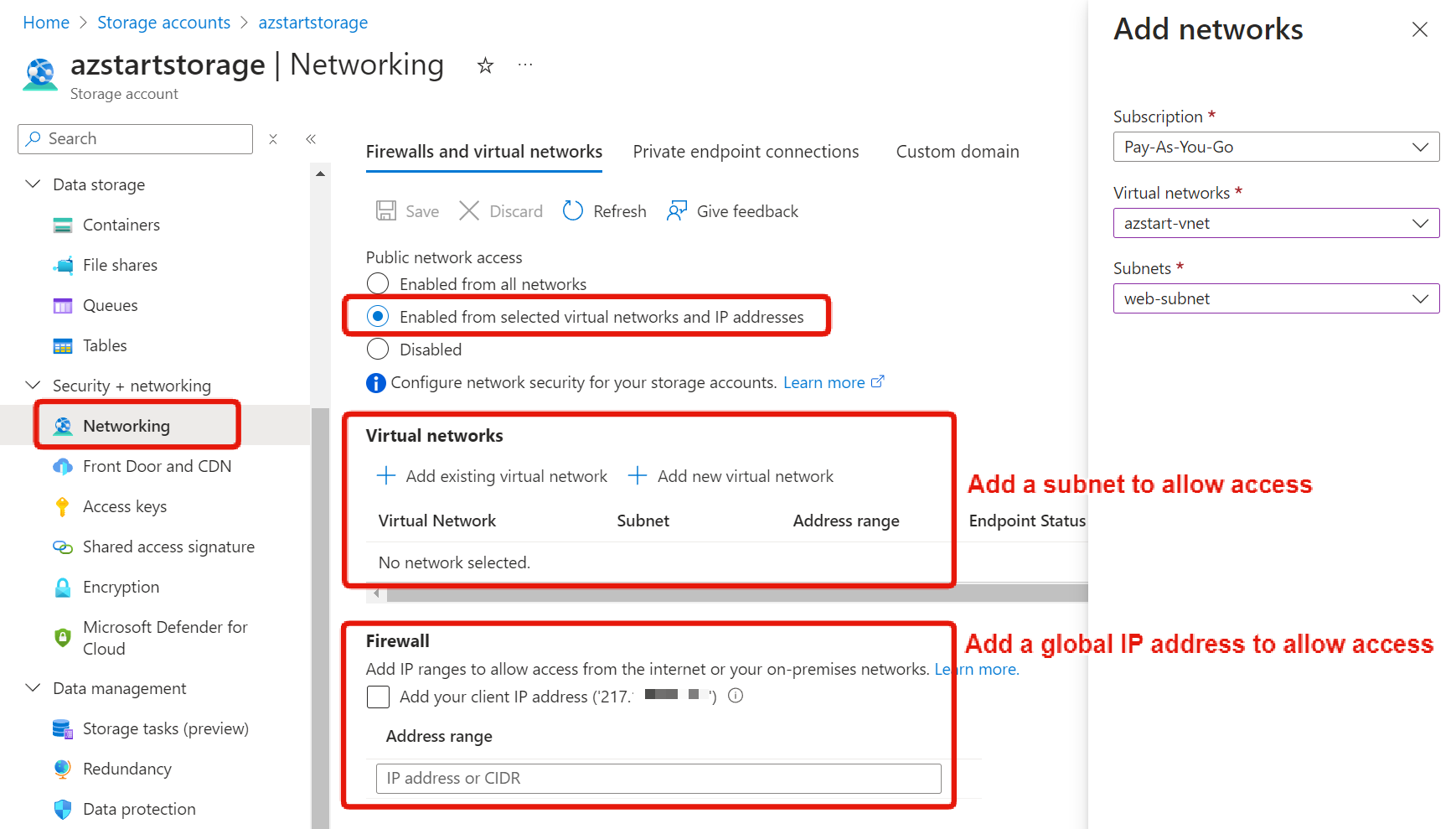
Note that in the Firewall section at the bottom, you can also specify an address range to allow IP addresses such as your PC.
To summarize, a service endpoint is like a gateway at the exit of a virtual network, serving as a transit point for public IP addresses of PaaS resources.
By routing connections from within the virtual network to PaaS through the service endpoint, you can connect securely and directly through the Azure backbone.
And by specifying virtual networks in firewall rules, you can restrict the source to specific virtual networks.
Key Points:
Using a service endpoint allows you to connect directly to PaaS resources through the Azure backbone, and you can restrict access to a specific virtual network.
While these features may seem very beneficial because they’re free to use, Microsoft recommends using “private endpoints,” which we’ll explain next.
This is because service endpoints can’t do things like “allow access only to certain resources” as a destination, even if the source can be restricted, and using public IP addresses as a destination can be cumbersome to manage.
What is a Private Endpoint?
Using a private endpoint allows you to connect to PaaS resources using private IP addresses for the destination as well. This is equivalent to VPC endpoints (interface type) in AWS.
In other words, you can treat PaaS resources as if they exist inside the virtual network.
This is a paid service, and you will be charged based on the amount of time you use it and the amount of data processed.
This service was introduced after service endpoints, and the number of supported PaaS services continues to grow.
When using private endpoints, the following three Azure resources come into play:
| Azure Resource | Description |
|---|---|
| Private Endpoint | Essentially a Network Interface Card (NIC) |
| Private DNS Zone | Resolves PaaS URLs to private IP addresses of the NIC |
| Private Link | One-to-one association between private endpoint and PaaS service |
Here’s a diagram to illustrate:
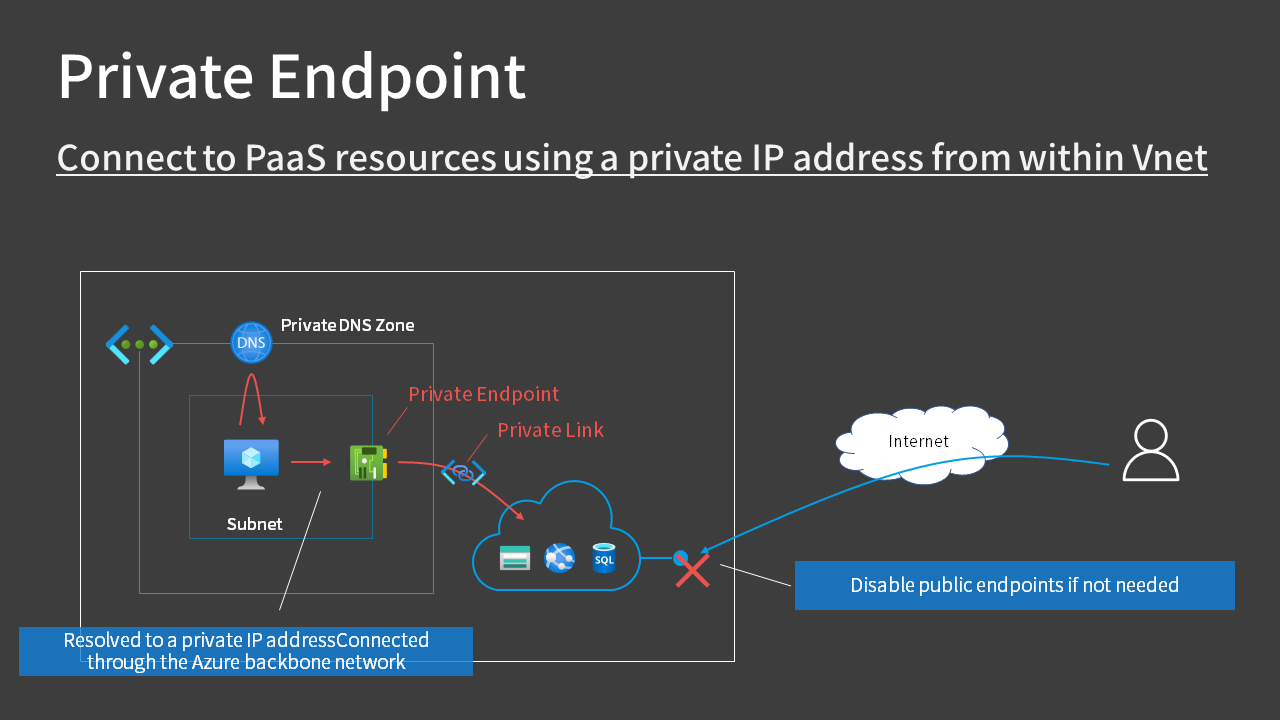
In the service endpoint described above, the PaaS connection URL is resolved to a public IP address. The route is no longer through the Internet, and the connection is made through the public IP address.
For a private endpoint, the PaaS connection URL is resolved to a private IP address.
The following screen shows an example of the result of name resolution using the dig command from a Linux virtual machine.
You can see that the URL for blob storage is resolved to a public IP address before the setting (top), but is resolved to a private IP address after the setting (bottom).
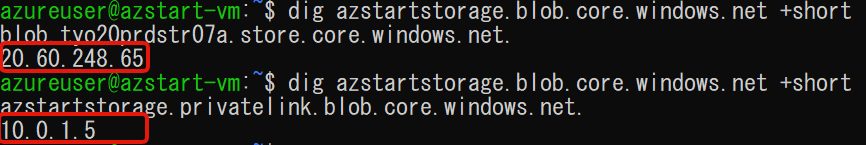
In other words, when connecting to the PaaS from the virtual network, the connection is changed to a private IP address by the entry in the private DNS zone, and the association (link setting) defined by the private link handles the relay accordingly.
It’s also worth noting that the association in the private link can be set one-to-one. Both the source and destination resources can be specified, taking into account the limitations of the service endpoints.
One point to keep in mind when actually using this is that the public endpoint isn’t automatically disabled, so if you want to block external access, you’ll need to disable public access.
Memo:
The difference between Private Endpoint and Private Link can be confusing, but the former refers to the NIC, while the latter refers to the association settings and routes. At first, it’s okay to think of them as the same thing.
Reference:
There’s also a feature called “Azure Private Link service” for private connection to custom services behind a load balancer, but it’s not covered in this article.
Private endpoints are created from the “Private Link Center” menu.
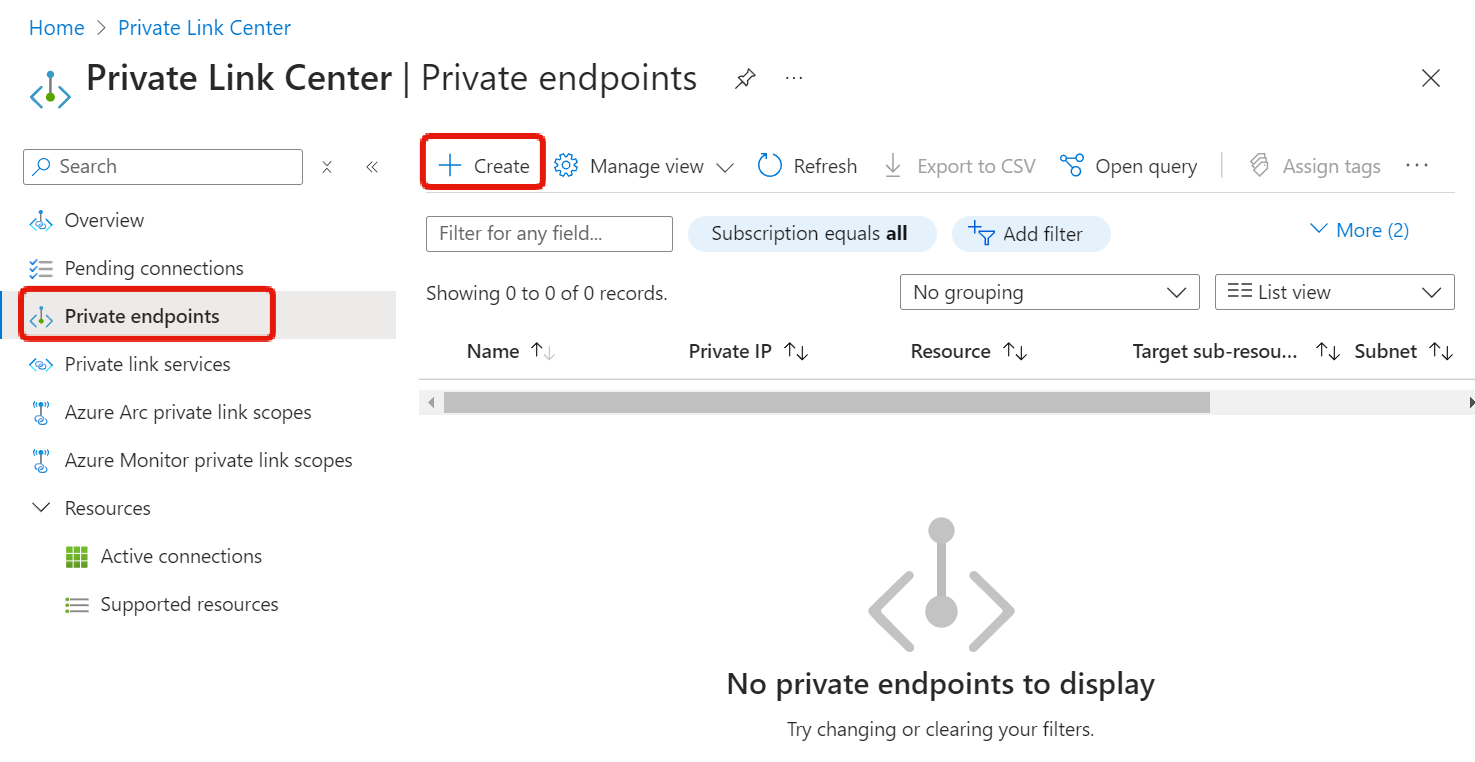 In the Basics tab, you specify the name and region.
In the Basics tab, you specify the name and region.
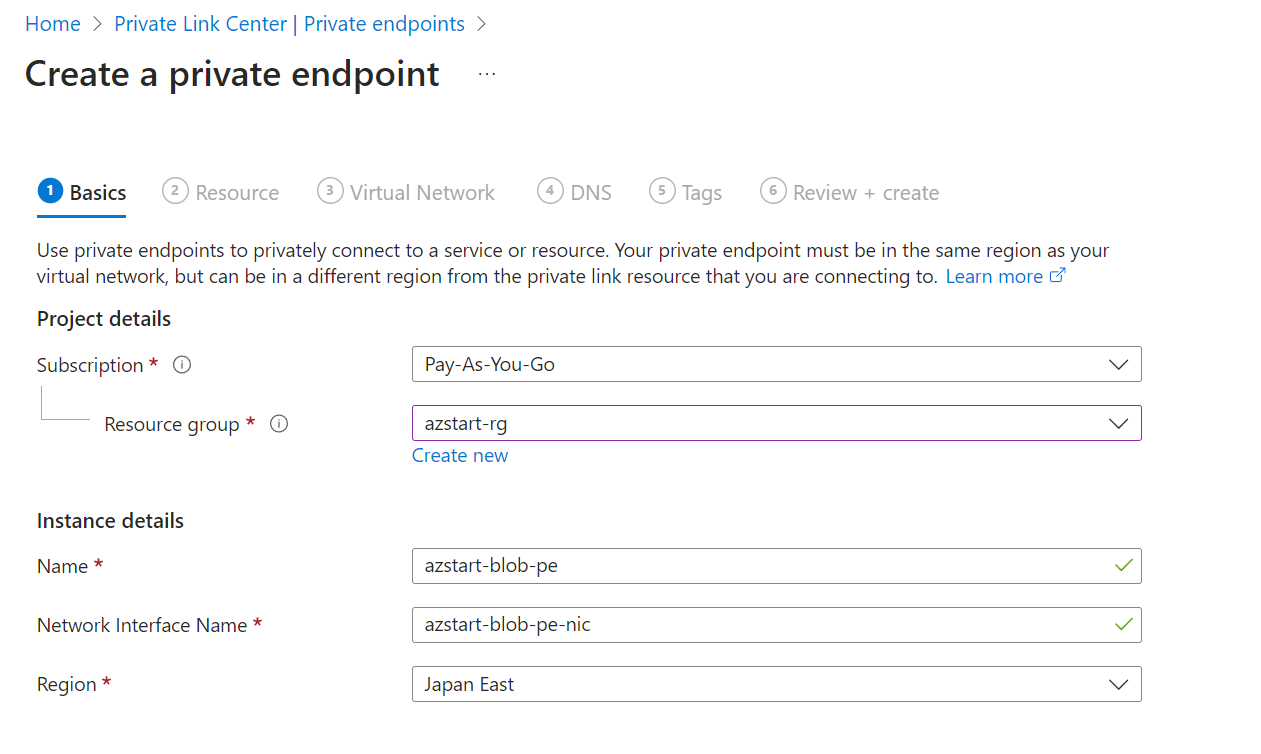
In the Resource tab, select the resource you want to connect to. Here we’ll select BLOB from a storage account.
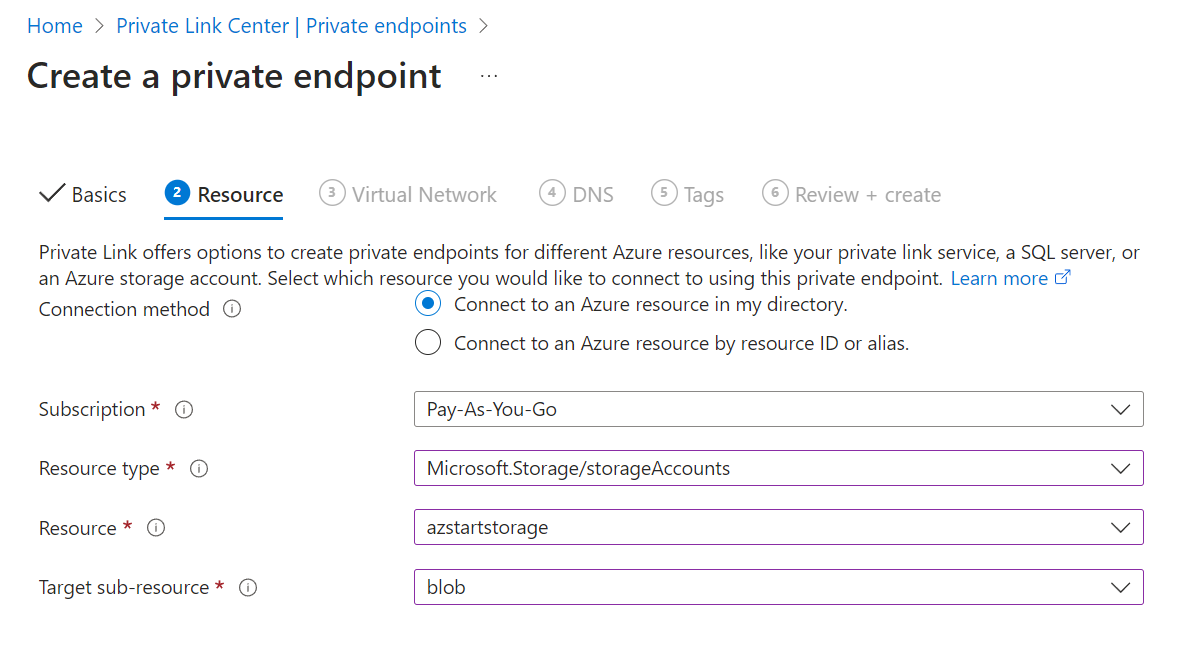
In the Virtual Network tab, you specify the source virtual network and subnet. A NIC will be created in the subnet specified here.
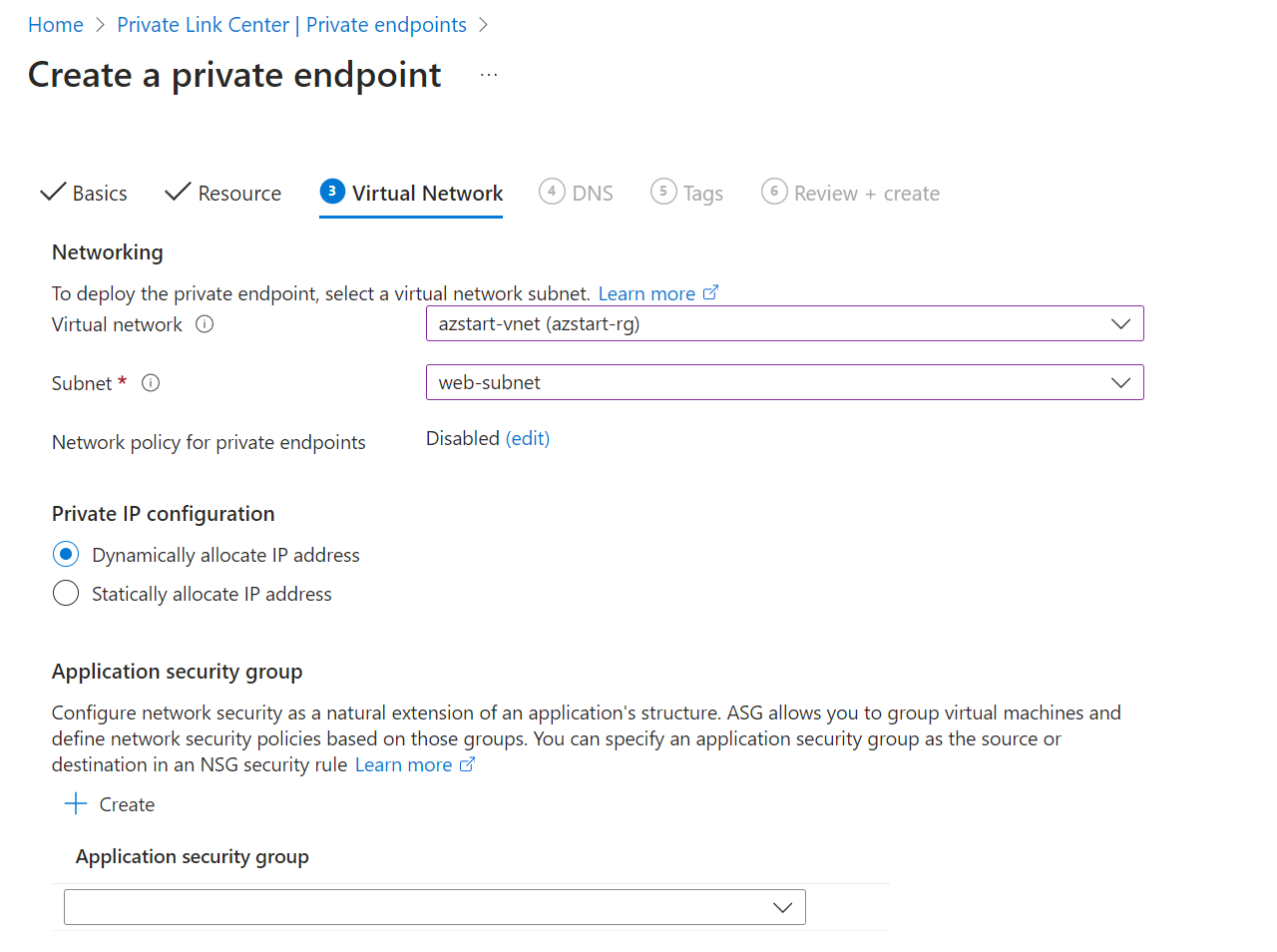
In the DNS tab, you specify how to manage DNS records. If you select “Integrate with private DNS zone” for Azure management, a private DNS zone will be created along with it.
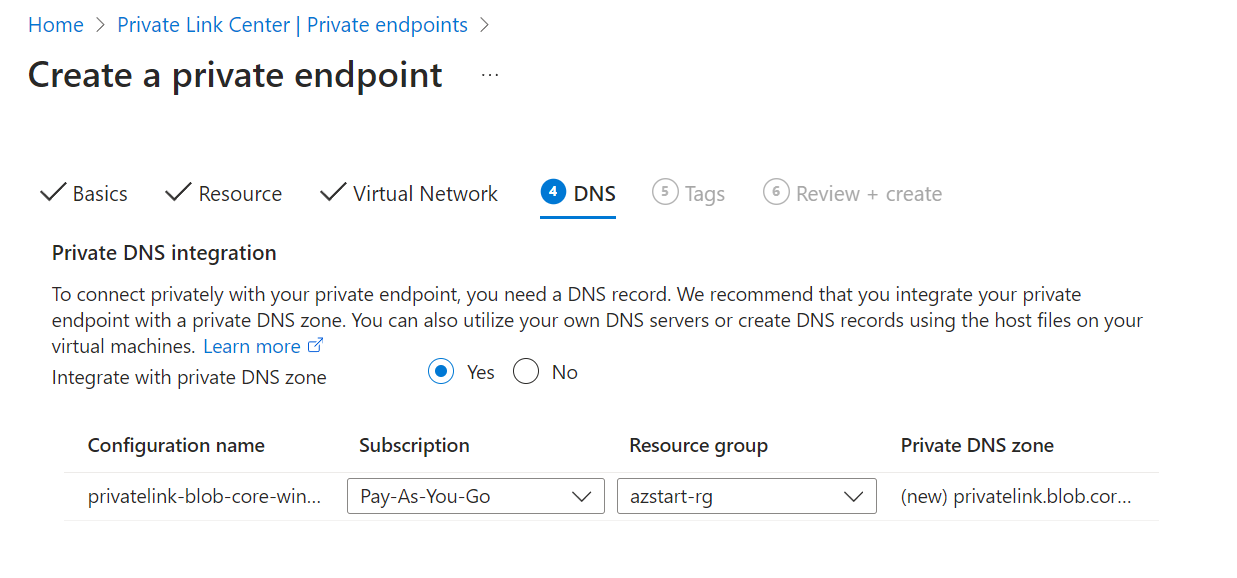
After you create a private endpoint, it’s a good idea to disable public access. However, this will prevent you from viewing content such as BLOBs from the Azure portal, so you may want to allow only specific IP addresses (depending on your security requirements).
You can also create private endpoints from the Network menu on the Resources page.
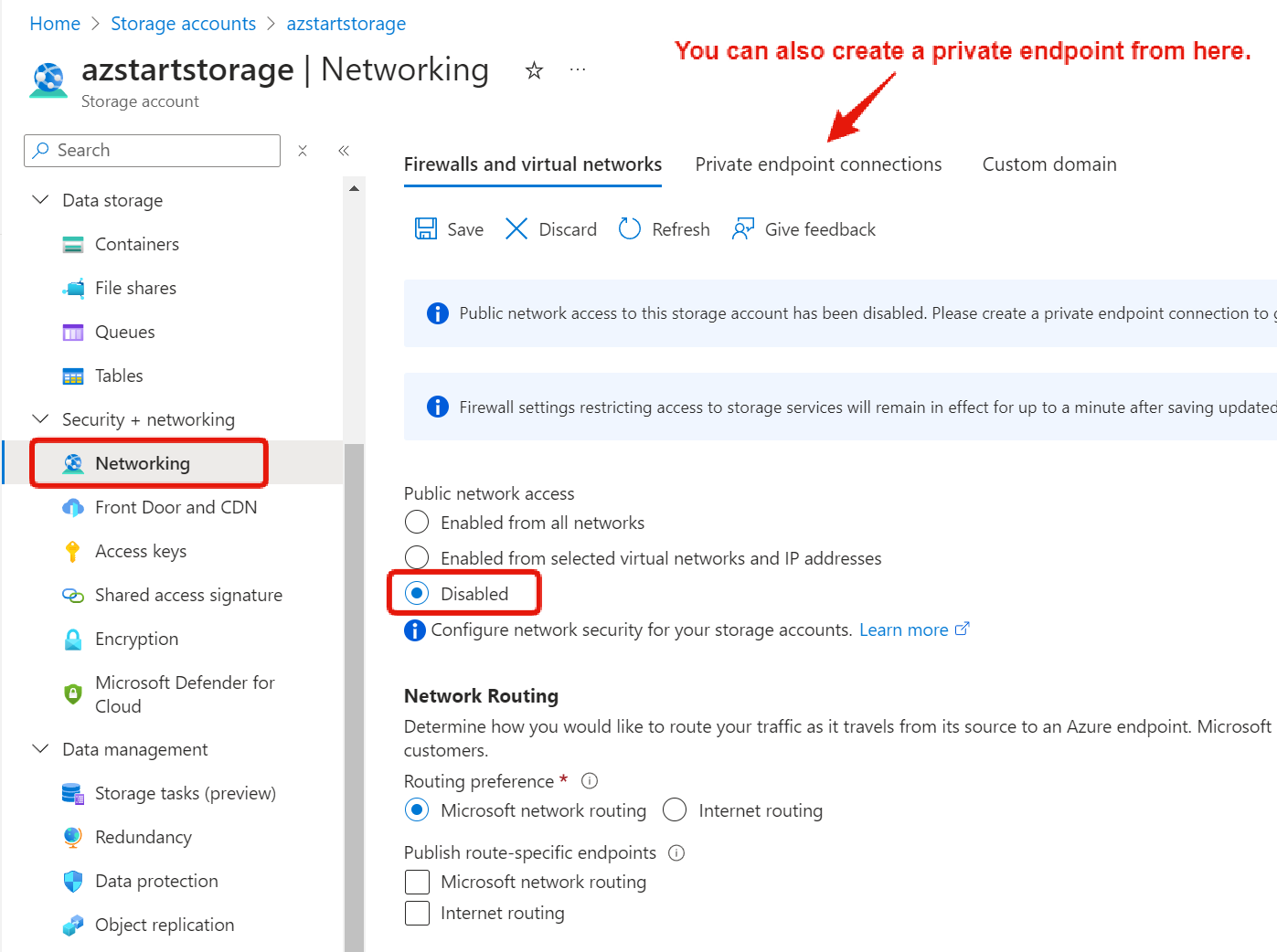
Finally, let’s confirm the connection from a virtual machine. Before, if it was not allowed by the firewall, we would get an error saying “The request may be blocked”. But after creating a private endpoint, we can now get the list of BLOBs.
$ az storage blob list --auth-mode login --account-name azstartstorage --container-name image --output table
The request may be blocked by network rules of storage account. Please check network rule set using 'az storage account show -n accountname --query networkRuleSet'.
If you want to change the default action to apply when no rule matches, please use 'az storage account update'.
$ az storage blob list --auth-mode login --account-name azstartstorage --container-name image --output table
Name Blob Type Blob Tier Length Content Type Last Modified Snapshot
------------------------- ----------- ----------- -------- -------------- ------------------------- ----------
course_image_Azure_IaaS.JPG BlockBlob Hot 60785 image/jpeg 2022-06-18T03:47:36+00:00
Summary
In this article, we explained about endpoints for connecting to Azure PaaS services.
Remember that by default, you connect over the Internet using a public endpoint, but there’s a method called a private endpoint for connecting securely in a closed network without going out to the Internet.
Also, private endpoints are often compared with service endpoints. Service endpoints can be used for free, so keep in mind that this method is also available.
See you next time.






 Source:
Source: 





