【AZ-900】What is Microsoft Entra ID? How is it different from Active Directory?

Hi, I’m Makoto, a freelance engineer.
In this article, I’ll explain Microsoft Entra ID (formerly Azure AD).
I’ll also clarify the differences with on-premises Active Directory, which can be confusing. Please read to the end.
Let’s get started!
Memo:
Azure AD changed its name to “Microsoft Entra ID” in October 2023. Only the name has changed; the functionality remains the same. For details, see the article Azure AD is Becoming Microsoft Entra ID.
Where are Administrator Accounts Registered?
Before we get to the main topic, let’s talk about Azure administrator accounts.
To sign up for Azure, you need a “Microsoft Account”.
In the article on creating a free account and signing up, we first introduce the procedure for creating a Microsoft account.

When you sign up for Azure, this Microsoft account is registered as an initial user with administrative privileges, so you can log in to the Azure portal to create resources and add new users. It’s like the root user in Linux or the administrator in Windows.
Now, where is this administrator account (Microsoft account) registered?
The correct answer is that it’s registered in Microsoft Entra ID.
What is Microsoft Entra ID?
Microsoft Entra ID (formerly Azure AD) is a cloud-based service that provides identity and access management.
It serves as a “container” for managing information about users, devices, and other organizational elements.
Initially, it is sufficient to understand it as “container for users (people) = a system for user management”. The following explanations are also based on the user.
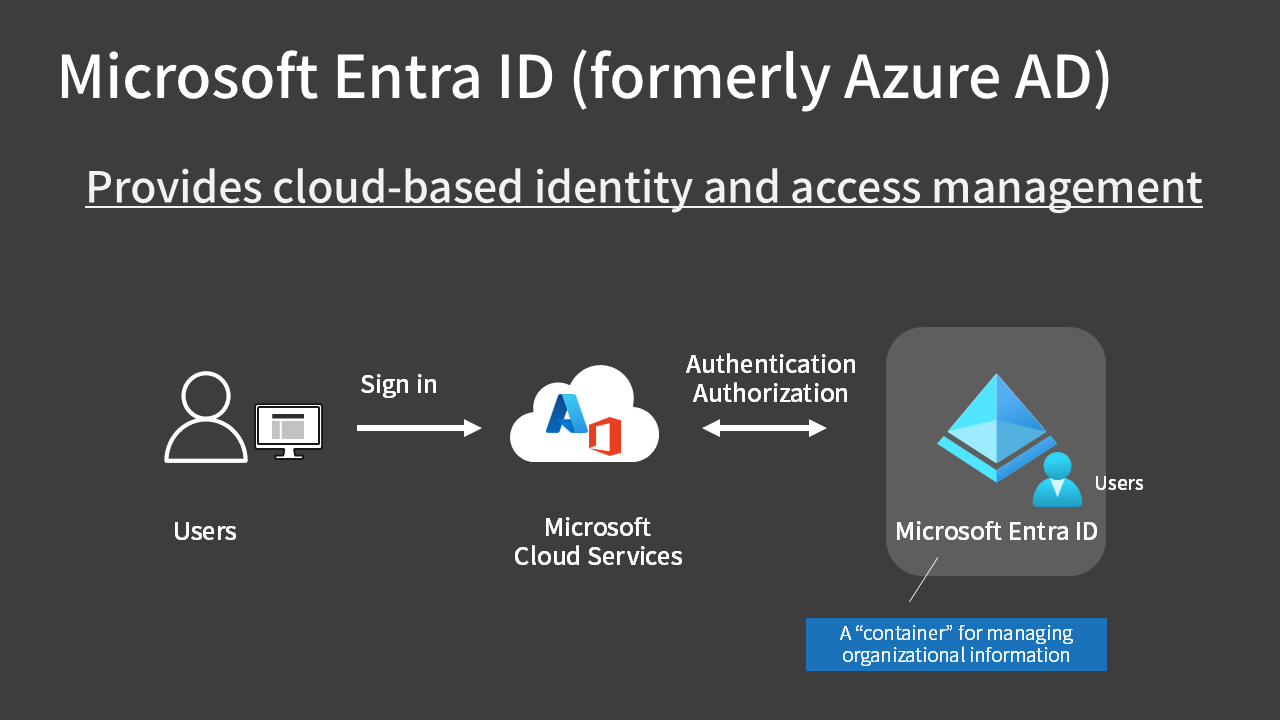

Identity and Access Management is a mechanism to authenticate who someone is and authorize (allow/deny) what they can do with what.
Microsoft Entra ID has the following characteristics:
- Because it’s cloud-based, there’s no need to set up new servers
- It has four editions, including a free plan and paid plans like Premium P1 and Premium P2 (the free plan doesn’t have an SLA)
- It’s used as the authentication foundation for Microsoft’s public cloud services beyond Azure, such as Microsoft 365 and Dynamics 365
- It’s a completely separate service from traditional, on-premises Active Directory (more on that later)
Behind the scenes, when you enter your user ID and password to sign in to the Azure portal, your Microsoft Entra ID is actually being used.
Authentication and Authorization
Microsoft Entra ID manages user IDs and provides authentication and authorization capabilities.
The terms “authentication” and “authorization” are often used in the context of access management. Let’s take a look at their differences.
Authentication
Authentication is the process of verifying the identity (who they are/credentials) of a user accessing a resource. In short, it’s “identity verification”.
Authentication methods are broadly classified into three categories:
- Use something you know, such as a password
- Use something you have, such as a cell phone
- Use biometric information, such as faces and fingerprints
Authorization
Authorization is the process of granting access rights (what can be done) to authenticated users or deciding whether to allow access.
It’s based on combinations of target resources and permitted operations, such as “allow starting/stopping virtual machines”.
Key Points:
Authentication
Verifying the identity of the user accessing
Authorization
Granting access rights to authenticated users or deciding whether to allow access
Tenants and Directories
Microsoft Entra ID is automatically created behind the scenes when you sign up for Azure.
More specifically, a “directory” is created within a “tenant” of Microsoft Entra ID, and “users” are registered within that directory.
Tenants and directories have a one-to-one relationship, so they’re often used interchangeably (which can be quite confusing…).
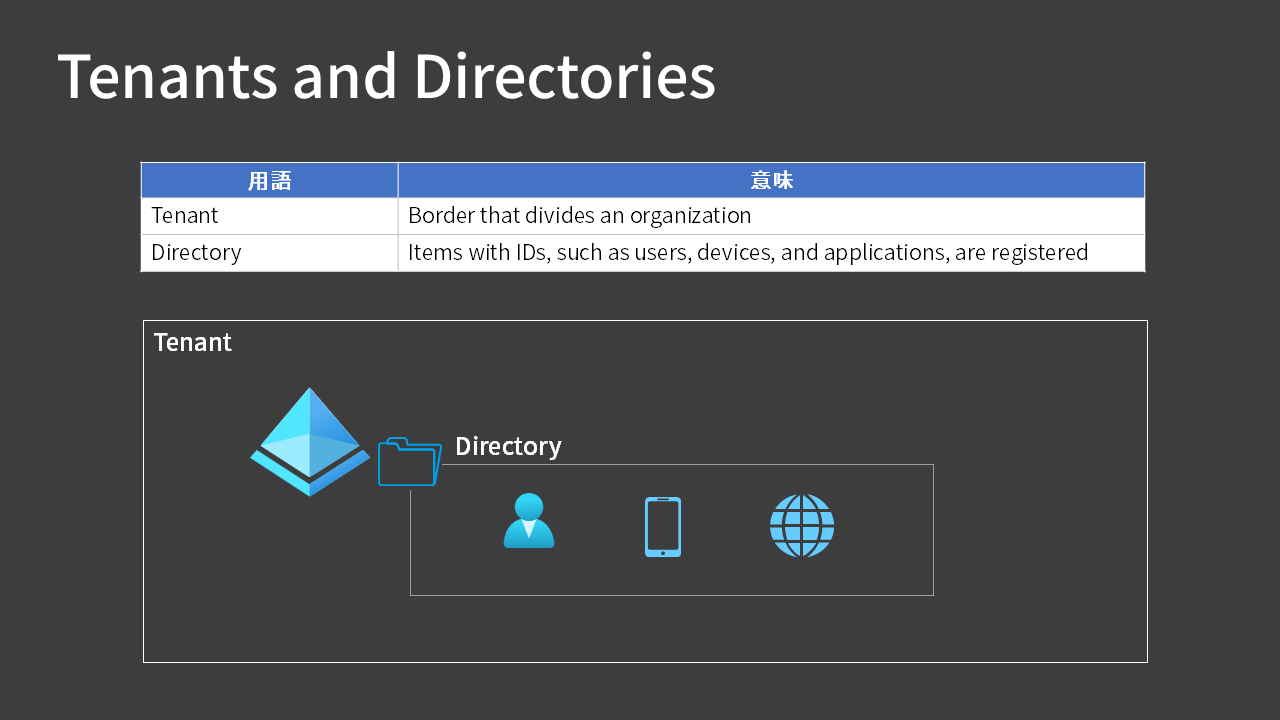

Tenants divide organizations, and items with IDs such as users, devices, and applications are registered within the directory, but frankly, I don’t think it’s necessary to strictly understand this difference.
For AZ-900 exam preparation, it’s probably enough to recognize these as terms related to Entra ID.
Reference:
If your organization is using Microsoft 365, a Microsoft Entra tenant should already be created.
If you additionally contract with Azure, completing the Azure sign-in with the Microsoft 365 admin account will associate two cloud services, Microsoft 365 and Azure, with the Microsoft Entra tenant.
Differences from On-Premises Active Directory
Active Directory Domain Services (ADDS)
The Active Directory used on-premises is officially called “Active Directory Domain Services“, sometimes abbreviated as ADDS, but more commonly just called AD.
Reference:
To make it easier to distinguish, we write “on-premises”, but it might be more accurate to say “a feature of Windows Server”.
For those familiar with on-premises AD (ADDS),
you may be wondering.
While they’re the same in terms of authenticating IDs, their purposes, network configurations, protocols, etc., are different. Despite similar names, they’re completely separate and incompatible.
| Microsoft Entra ID (formerly Azure AD) | On-premises AD | |
|---|---|---|
| Purpose | Authentication for cloud services | Authentication for internal resources |
| Network | Internet | Intranet |
| Assumed security model | Zero Trust | Traditional Perimeter Security |
| Protocols | SAML, OpenID, OAuth | LDAP, Kerberos |
In this case, it’s just that the intranet (internal network) has changed to Azure’s VNET, but the mechanism is the same as on-premises AD (ADDS). It’s a form where the domain controller exists on Azure.
Microsoft Entra Domain Services
To make things even more complicated, Azure has a PaaS version of on-premises AD (ADDS) called “Microsoft Entra Domain Services“. (formerly Azure AD Domain Services)
Because it’s a managed service, there’s no hardware or operating system to manage, and you can use domain controller capabilities without setting up virtual machines.
We can see that there are broadly three types of Microsoft services for managing IDs (directory services):
- Microsoft Entra ID
- ADDS (on on-premises physical servers or Azure VMs)
- Microsoft Entra Domain Services (PaaS version of ADDS)
Key Points:
Remember that Azure provides the following two types of directory services:
- Microsoft Entra ID (formerly Azure AD)
- Microsoft Entra Domain Services
Reference:
Although Microsoft Entra Domain Services is compatible with Windows Server Active Directory, it has some limitations and isn’t a complete replacement for on-premises AD.
Creating Users and Groups
To use Azure in an organization, you must first create users. Typically, the Administrator account is not used for day-to-day tasks.
You can create new users from the Users menu in Microsoft Entra ID.
You can also streamline the process of granting access rights and licenses by assigning users to groups.
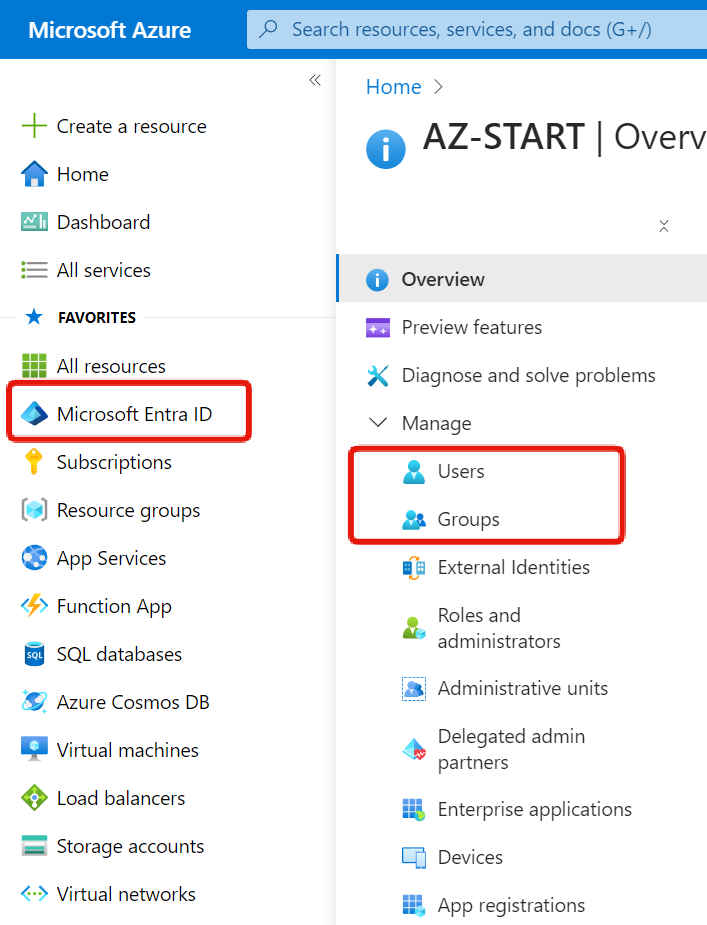

Creating Users
Open Users to see a list of all users. If you are inviting external users, their user type will be Guest.
To create a user, click “Create new user”.
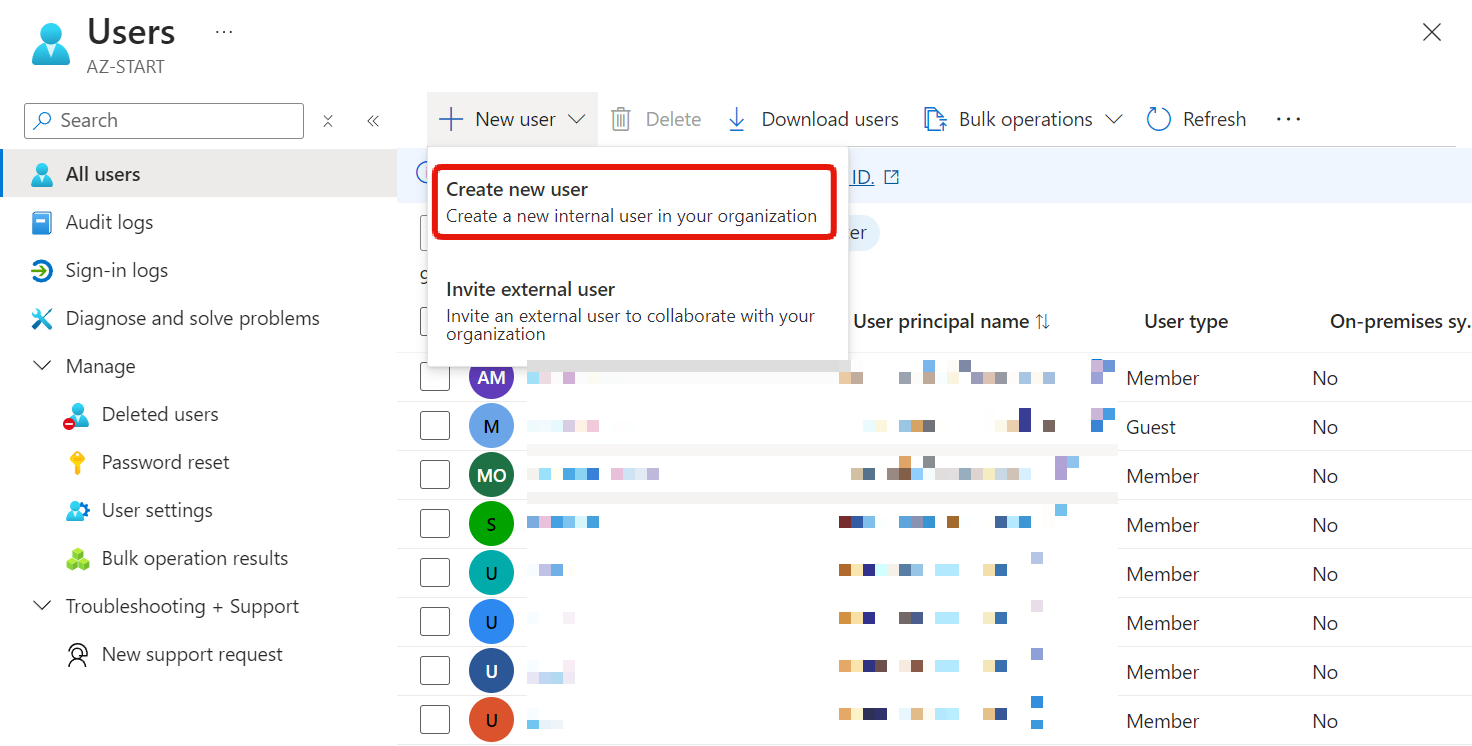

Register your username and password. The password registered here is only an “initial password”, so you will need to change it the first time you sign in.
You can specify a group when creating a user, but you can also add them to a group later.
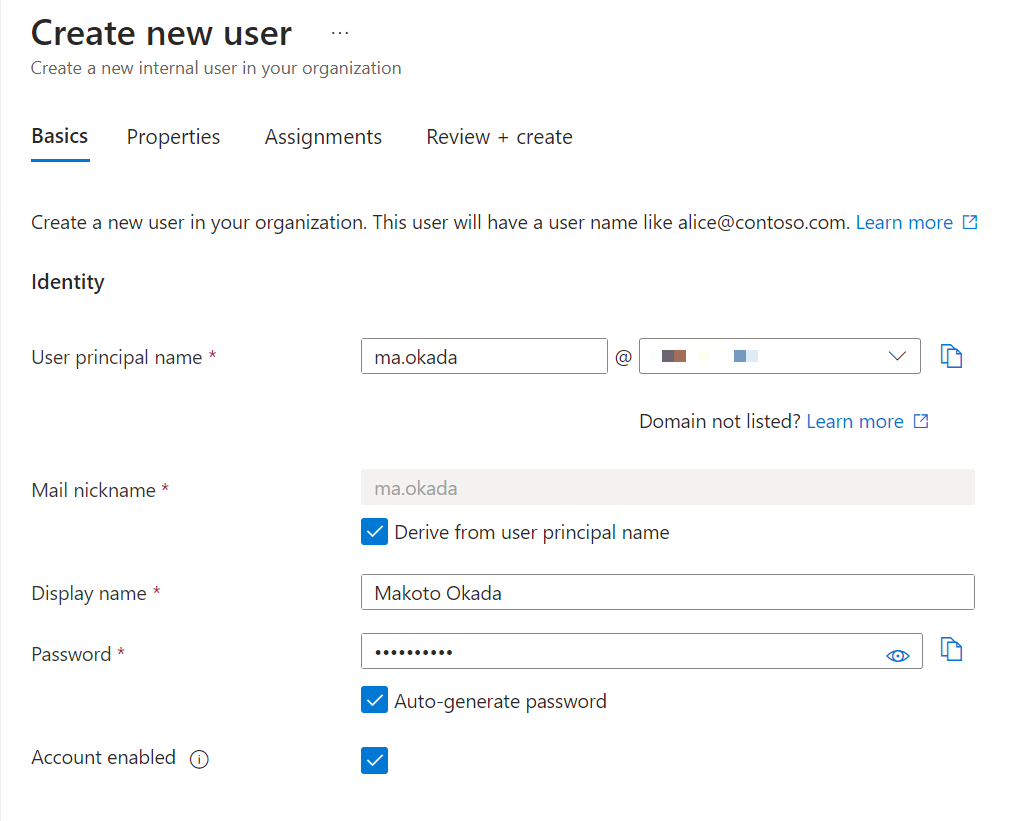

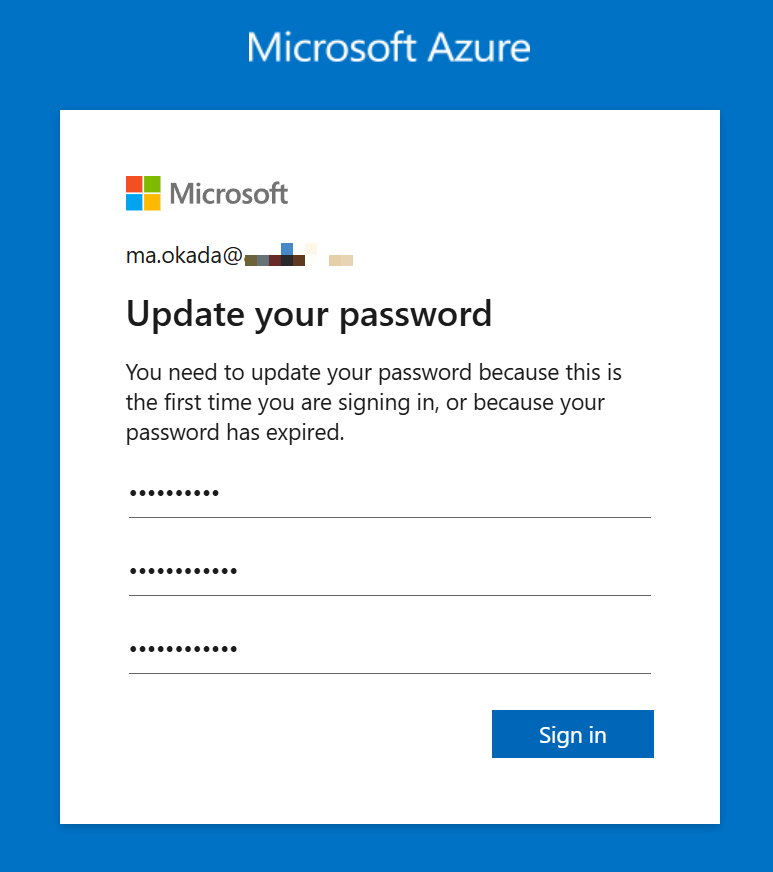
After entering the user ID and initial password, update the password and sign in.

Inviting Guest Users
By clicking on “Invite external user”, you can register external users as guest users. Conversely, “Create new user” is for creating users within your organization.
You can use this method to register users when you invite collaborating companies, such as the System Integrator (SI) that the user company has hired to build the system and continue development together.
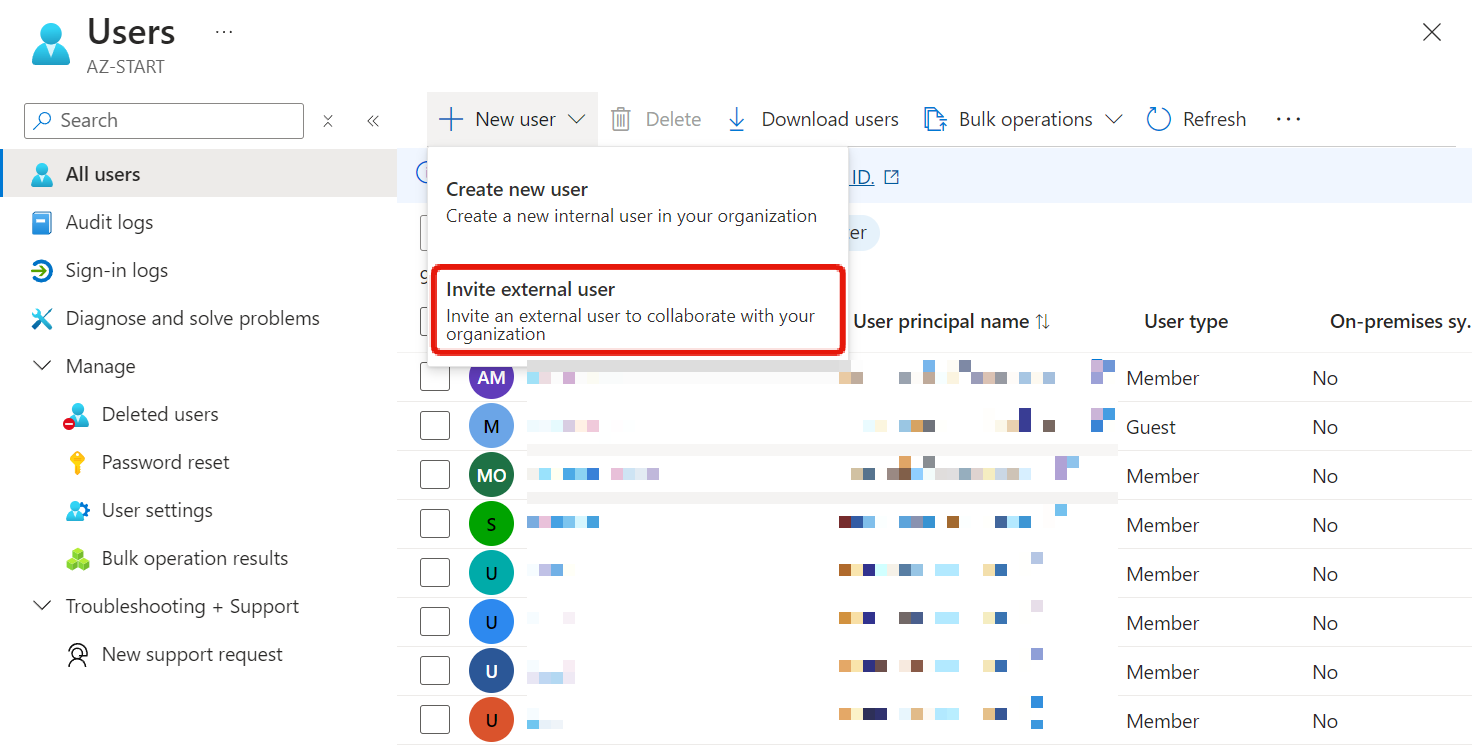

When you invite by entering a corporate email address or a social account such as Gmail, an invitation email is sent to that person. Once they accept, they are enrolled in Microsoft Entra ID and can sign in to the Azure portal using that email address.
Synchronizing from On-Premises AD
If you already have Active Directory in your on-premises environment, you can use Microsoft Entra Connect (formerly Azure AD Connect) to synchronize objects such as users and groups registered in the on-premises AD with the Microsoft Entra ID.
Microsoft Entra Connect is installed and configured on the on-premises AD server.
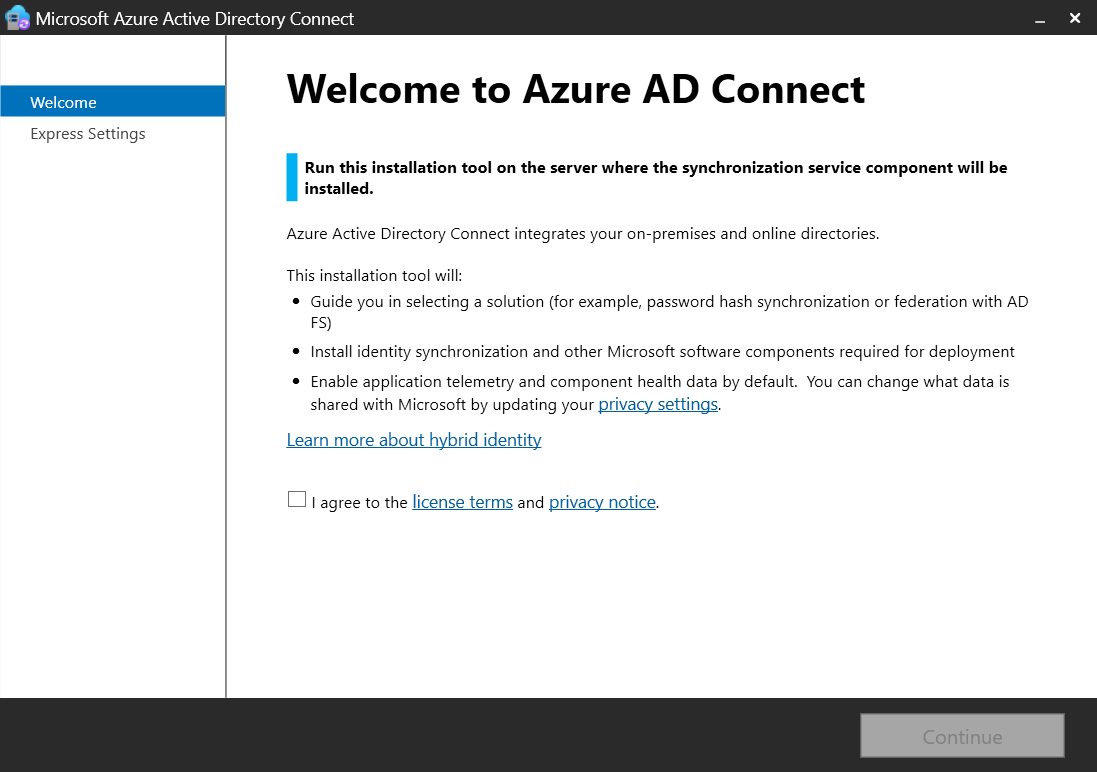

After synchronization, you can sign in to Azure with IDs registered on-premises.
Remember this as a means of using IDs in a hybrid environment that integrates on-premises and Azure.
Key Points:
Microsoft Entra Connect
Used when synchronizing on-premises Active Directory with Microsoft Entra ID.
Creating Groups
In the Groups menu, all groups are listed, and you can create new ones from “New group”.
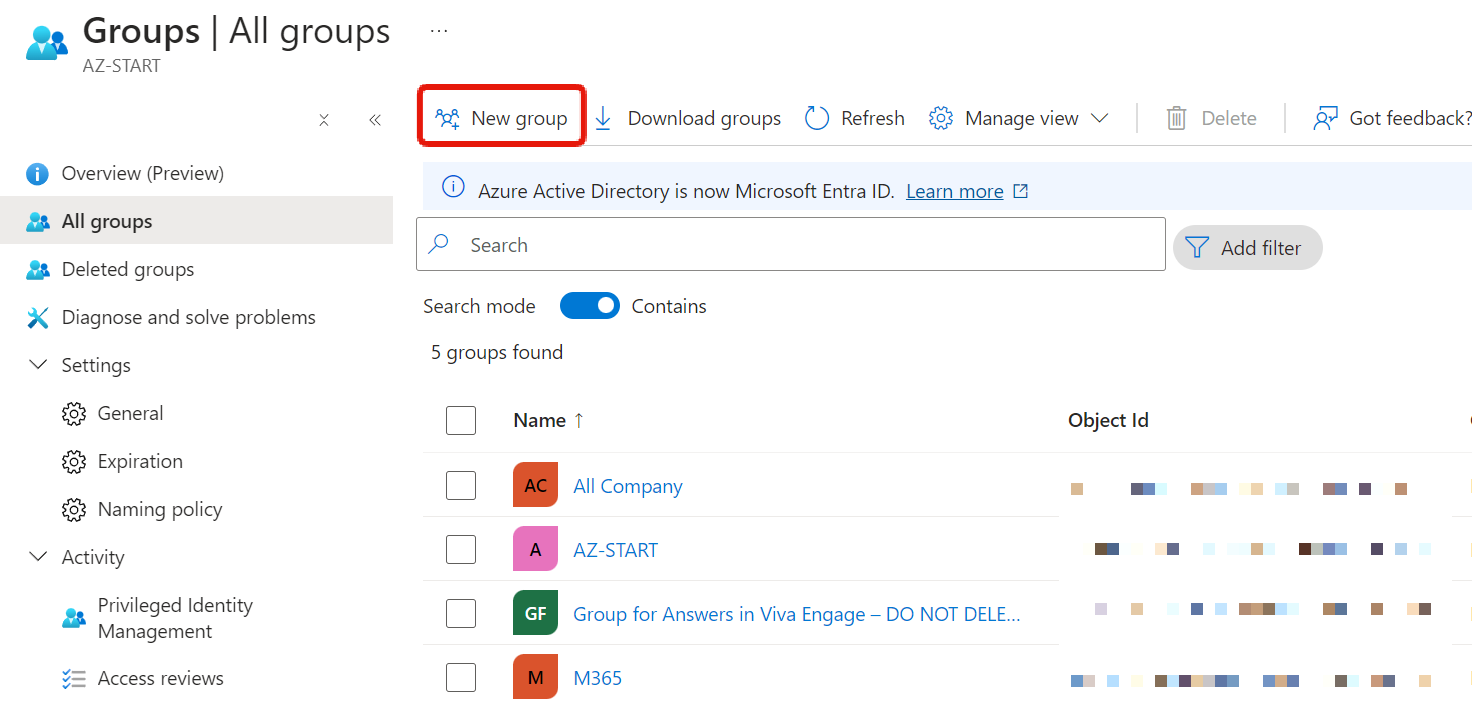

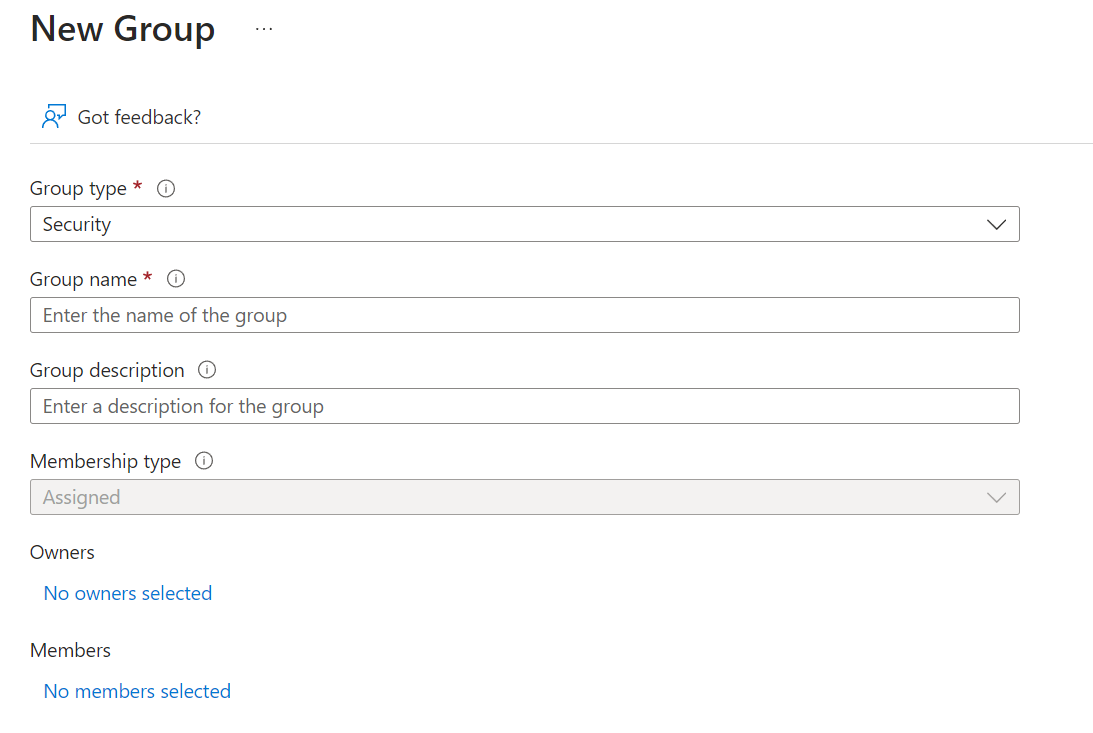
Enter the group name and other details to create it.
- Group types
- Security: Used to manage access to Azure resources
- Microsoft 365: Used to manage access (collaboration) to M365 tools
- Owners
- Register members to manage this group (optional)
Can be managed with an admin account even without registration
- Register members to manage this group (optional)
- Members
- Register members to belong to this group

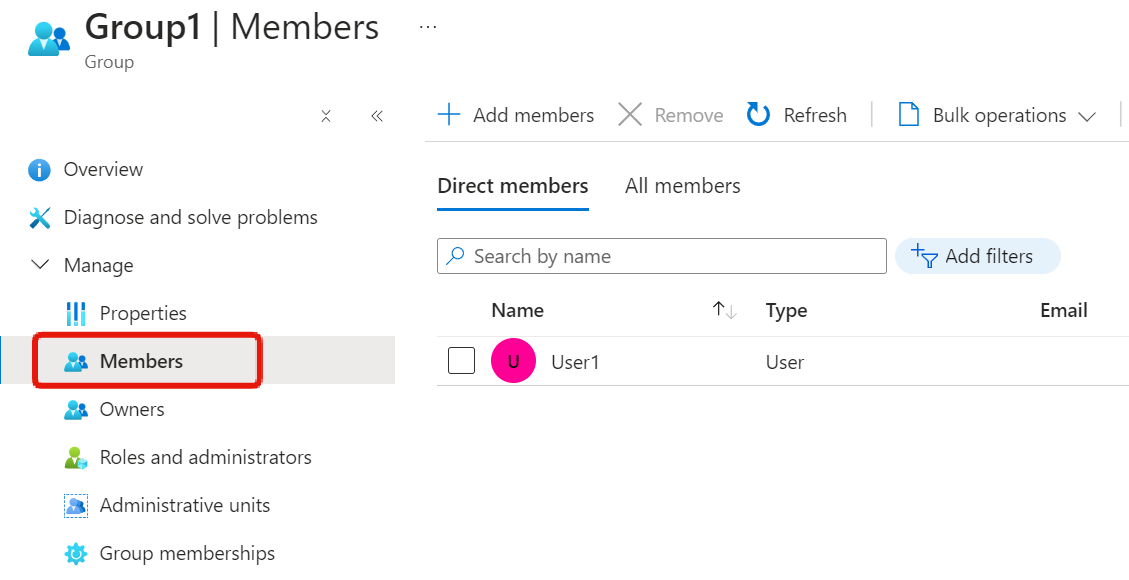

Summary
In this article, we explained Microsoft Entra ID. To summarize the key points of Microsoft Entra ID for AZ-900 exam preparation:
- Microsoft Entra ID is the common authentication foundation for Microsoft’s public cloud services
- It has a Free tier that can be used at no cost and paid license tiers such as Premium P1, P2
- There are three types of directory services:
- Microsoft Entra ID (formerly Azure AD)
- Active Directory Domain Services (ADDS)
- Microsoft Entra Domain Services (formerly Azure AD Domain Services)
- External users can be invited as guest users
In addition, the relationship between subscriptions and Microsoft Entra ID is important. Please also see this article.



See you next time.